How To Reduce Third-Party Risk - Part 3 of 4

Part 3: How to Reduce Non-Employee Access Risk: Maintain Trustworthy Data
In 2021, there were over 18 billion data records exposed. Many of these breaches were by insiders involved in malicious or accidental events. To manage the tsunami of exposed data, an environment that promotes ‘trustworthy data’ must be established. Maintaining trustworthy data is also a core requirement for addressing non-employee access risks, and centralization is paramount to achieving this goal.
Trustworthy data enables integrity and reliability
Creating a culture of trustworthy data means knowing who has access to what at all times – despite the dynamic nature of non-employee work engagements. This simple concept of maintaining integrity and reliability of data is the pivot upon which third party access management turns. Without a way to centrally assign access on a need to know and least privilege basis, access cannot be managed in the granular way that modern enterprises with disparate data require.
Trustworthy data breeds accountability
From service accounts to IoT devices, a lack of ownership in these often rouge elements can be a concerning problem in access management. This translates into a lack of accountability and raises questions as administrators attempt to manage devices. An IAM engineer may find themselves asking, “Who owns this SysAdmin account?” or “Who owns this switch or IoT device?” These gaps in data must be addressed to ensure robust access management. Accountability is a driver of trust, and to achieve accountability there must be clear ownership.
Trustworthy data is auditable
Auditability is a central part of building a trustworthy data culture. A centralized portal that onboards and manages the lifecycle of non-employees can be designed to track both data access and the access policies of the organization. When all non-employees are associated with the right system accounts, devices, and rules, essential tracking can be accomplished. This ultimately allows enterprises to conduct compliance checks and truly enforce access policies.
Trustworthy data requires governance
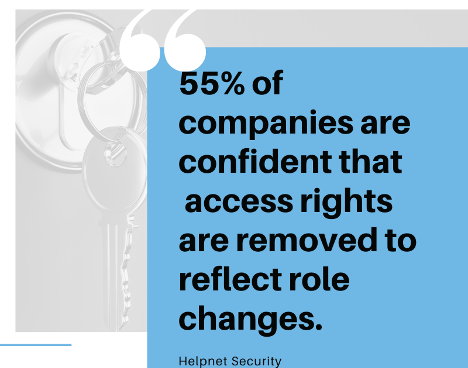
A survey into onboarding/offboarding, found that when employees (and non-employees) change roles in an organization, just over half (55%) of respondents felt confident that unnecessary access rights have been removed to reflect any role changes. The survey also highlights the fact that these changes are still largely manual processes, with 54% being entirely manual, and 37% using a combination of some automation and manual processes. The survey also pointed out that only 9% leveraged full automation.
The governance of non-employees (non-human accounts and third-parties) is a key feature of an effective identity and access management system. A centralized data-centric approach to third party access management, for example, can prevent situations where contractors are assigned to incorrect managers or no manager at all after a boss leaves the company. The system and associated processes should be automated to enable governance and preservation of trustworthy data.
By committing to the centralized data-centric management of non-employees, enterprises can resolve some of the most difficult issues around third-party identity and access management and accessing reliable, trustworthy data.



