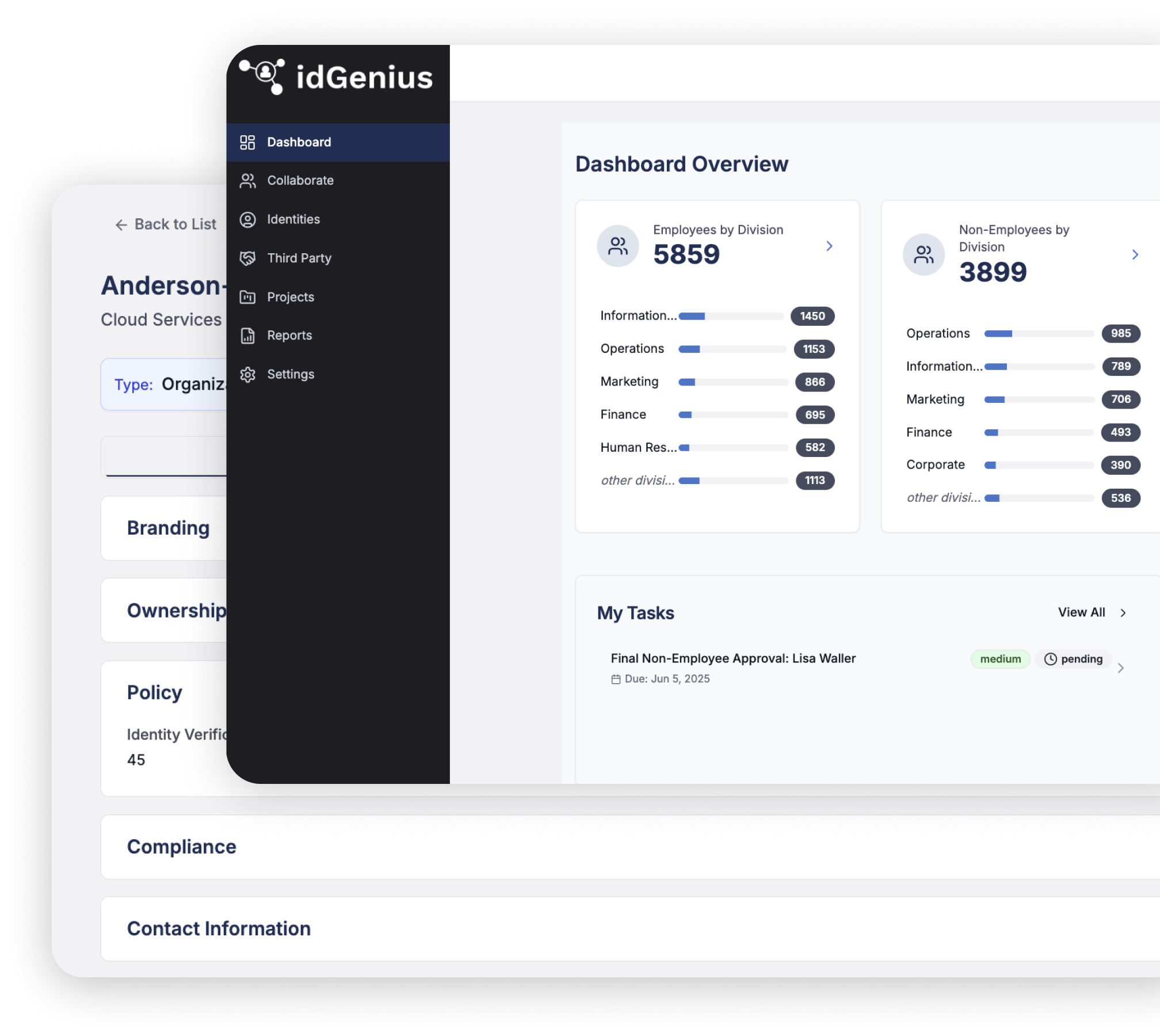
The idGenius Platform
Managing third-party identities has never been more critical. Whether it’s vendors, contractors, or business partners, your organization needs a reliable, AI-powered solution to reduce risk, enhance compliance, and improve operational efficiency.
idGenius by Anomalix provides an intelligent, SaaS platform designed to automate identity and third-party lifecycle management while enforcing zero-trust security.
Trusted by teams securing complex environments






























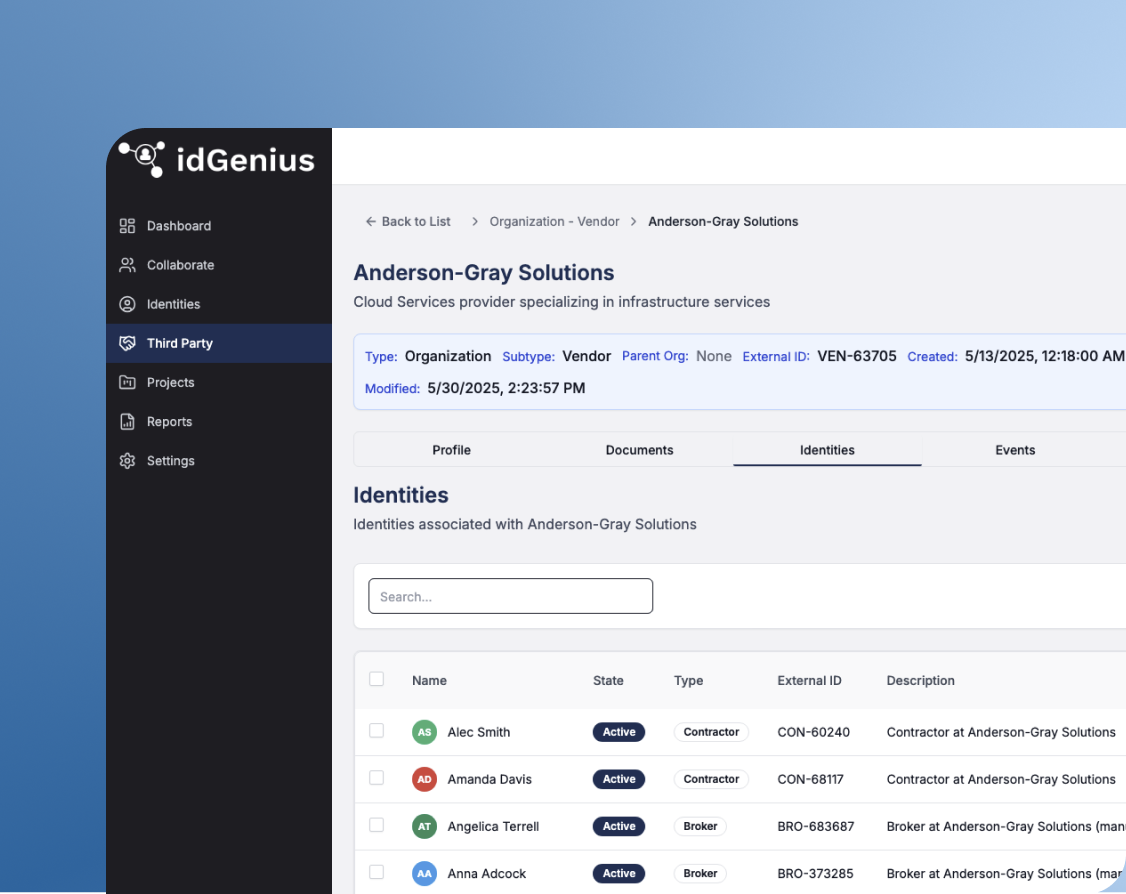
Secure vendor & third-party management
A centralized platform to control and monitor identities for vendors, contractors, brokers, and other third-party identities.
- Enforces policy-driven controls.
- Ties identities to projects, contracts, and business needs.
- Enables role-appropriate, time-bound access.
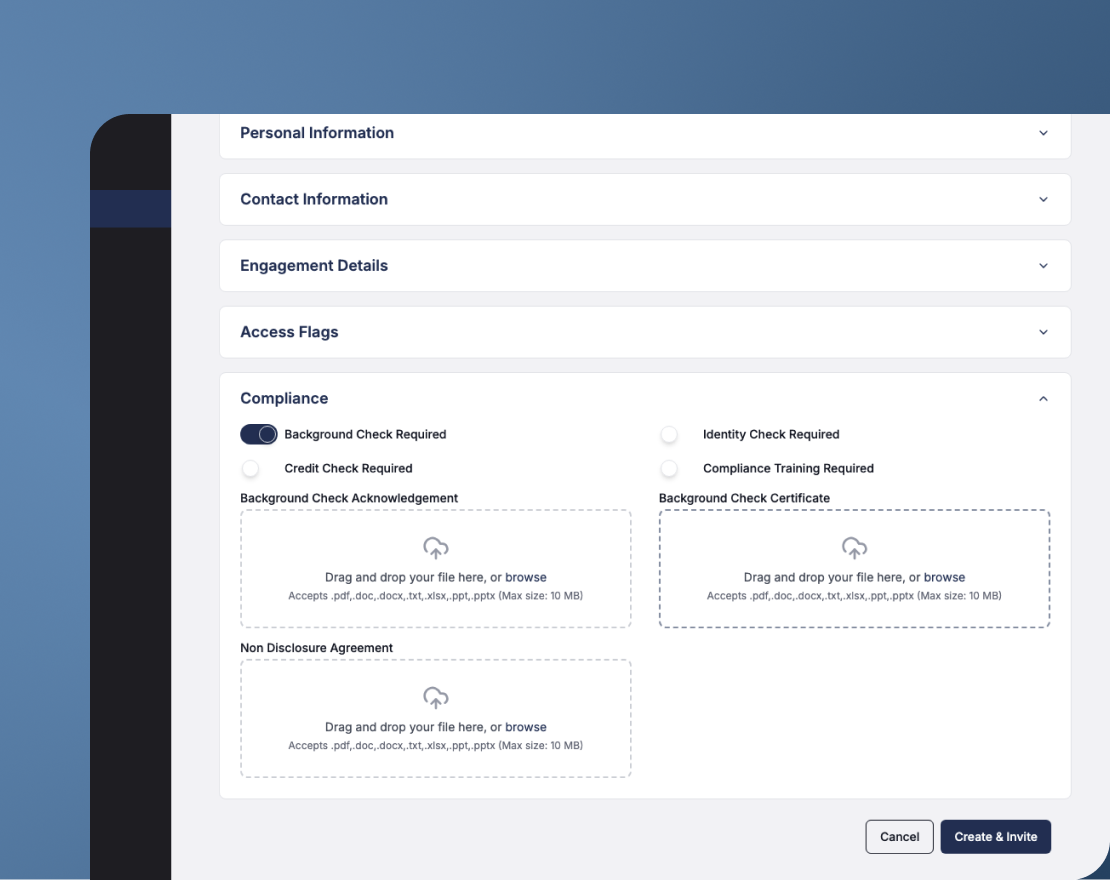
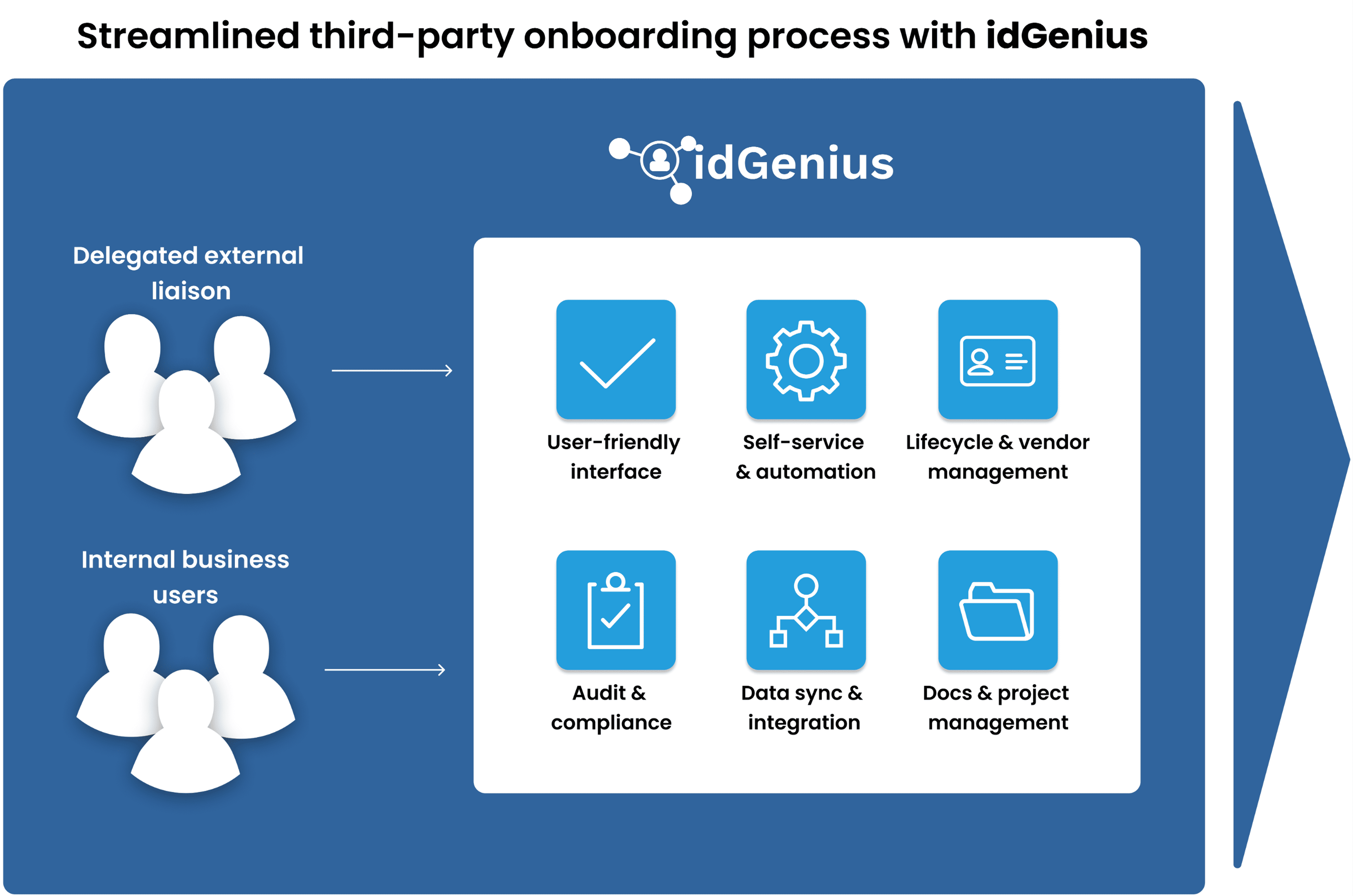
Automated onboarding with identity verification
Streamlined, no-code onboarding that incorporates trust-building workflows.
- Built-in background checks, credit checks, and identity verification.
- Custom onboarding forms with self-service capabilities.
- Enforces business logic to validate identities before access is granted.
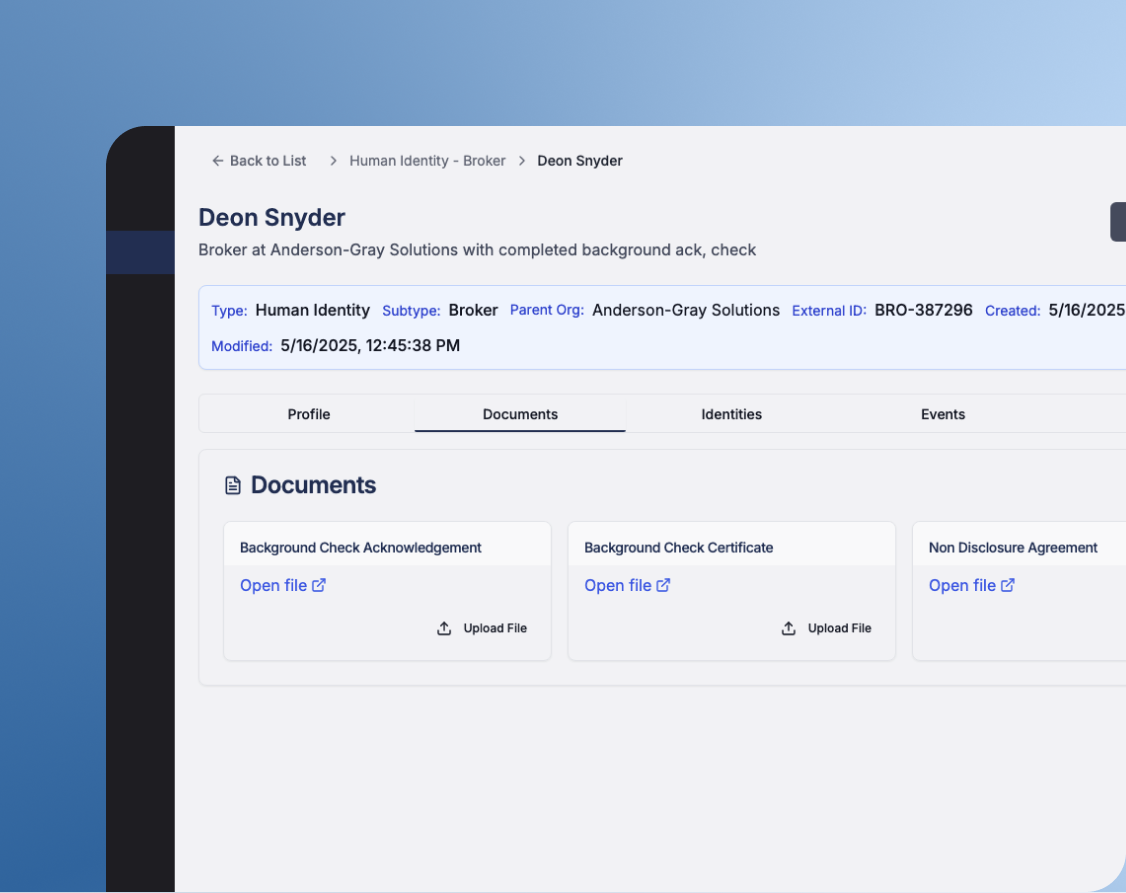
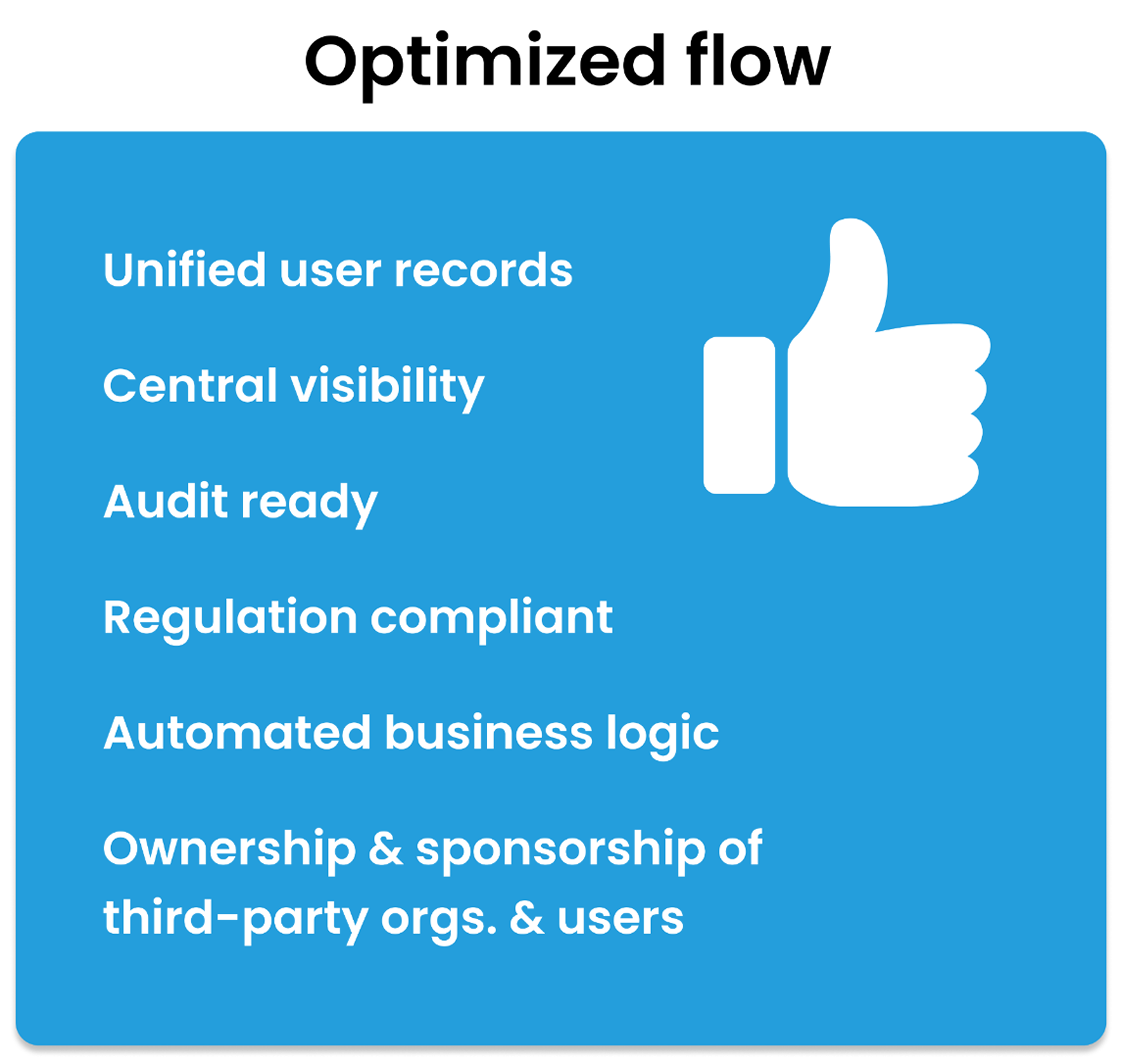
Centralized document & lifecycle management
Manages every stage of the identity lifecycle with governance and audit-readiness.
- Stores NDAs, contracts, credentials, training content, certifications, and performance history.
- Tracks start/end dates, sends expiration notifications, and triggers access reviews.
- Maintains full change history and audit logs.
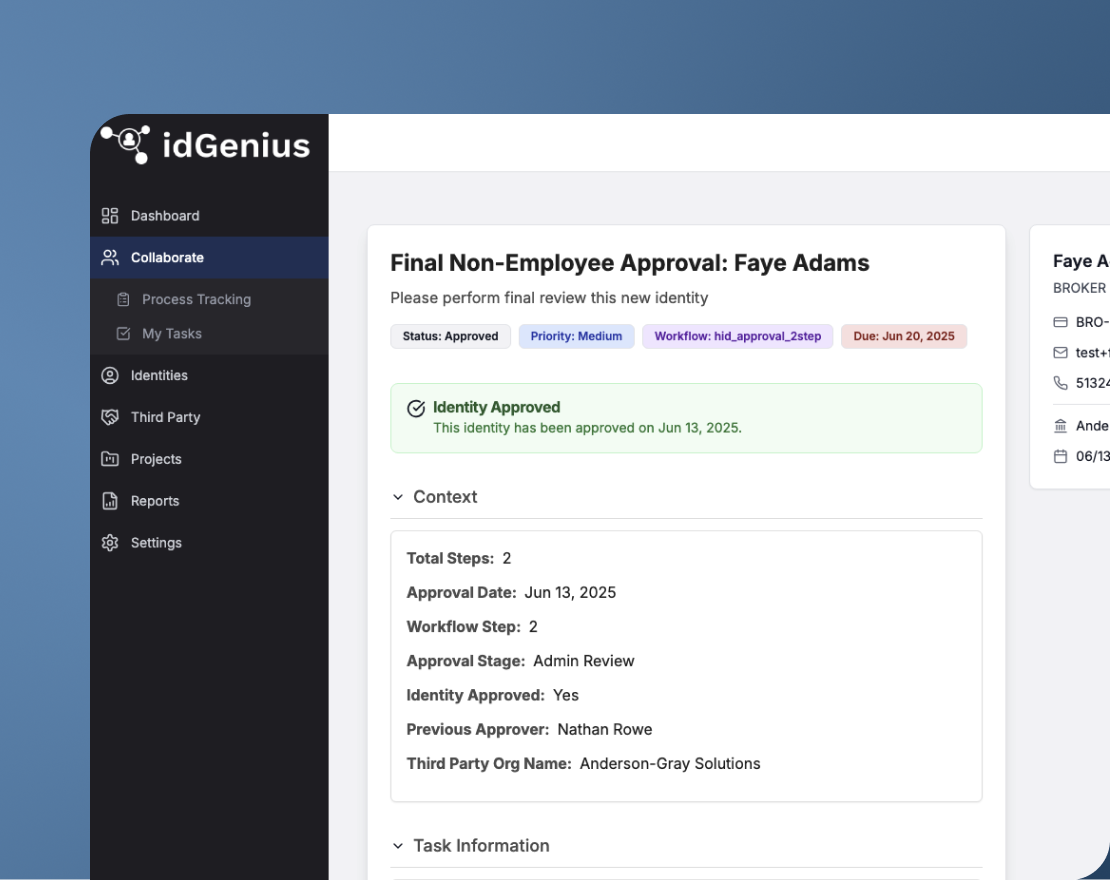
Streamlined approvals with delegated vendor review
Shift the initial approval responsibility to those who work directly with vendors—so that only pre-vetted, necessary access requests reach business admins for final review.
- Vendor managers validate access needs before escalation.
- Business admins review fewer, higher-quality requests.
- Preserves oversight with final approval only given by business admins.
Who benefits from idGenius?
- Retail and Maufacturing organizations managing vendors, suppliers, contractors & consultants
- Healthcare and Life Sciences organizations securing third-party access to providers and research institutions
- Insurance and Financial Services managing affiliated brokers and agents
- Government and Defense agencies ensuring regulatory compliance and security clearances
How idGenius comes into play
idGenius empowers organizations to take control of third-party risk through AI-driven automation:
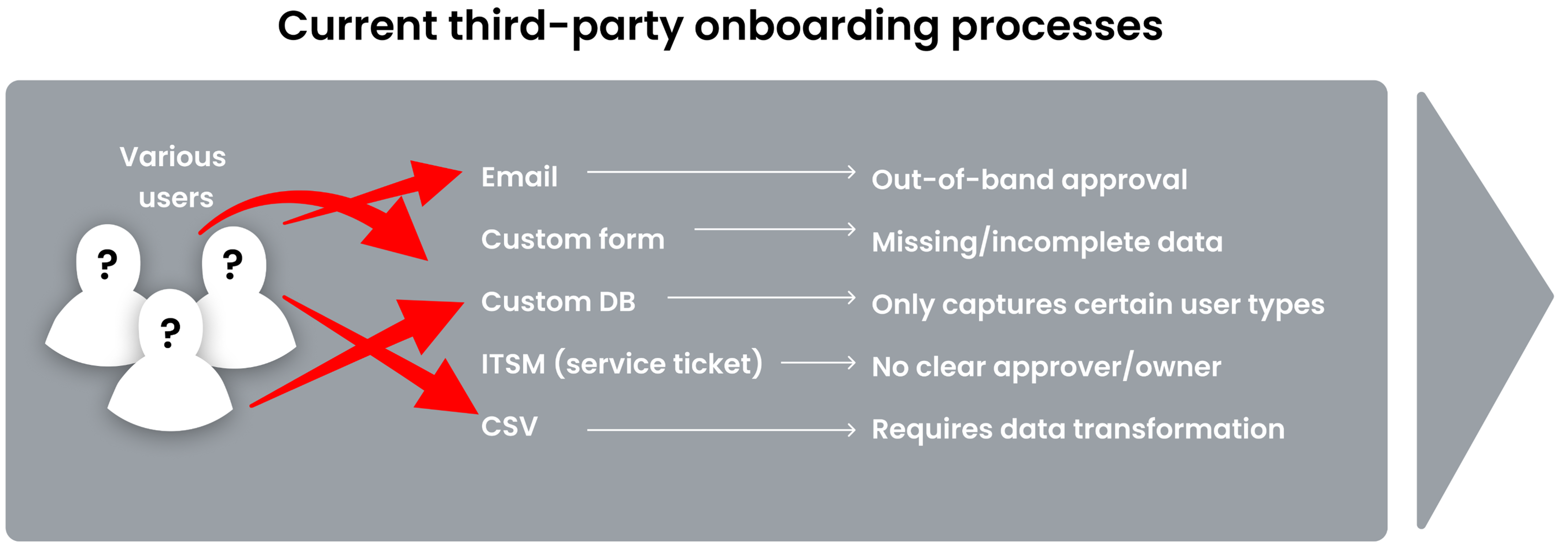
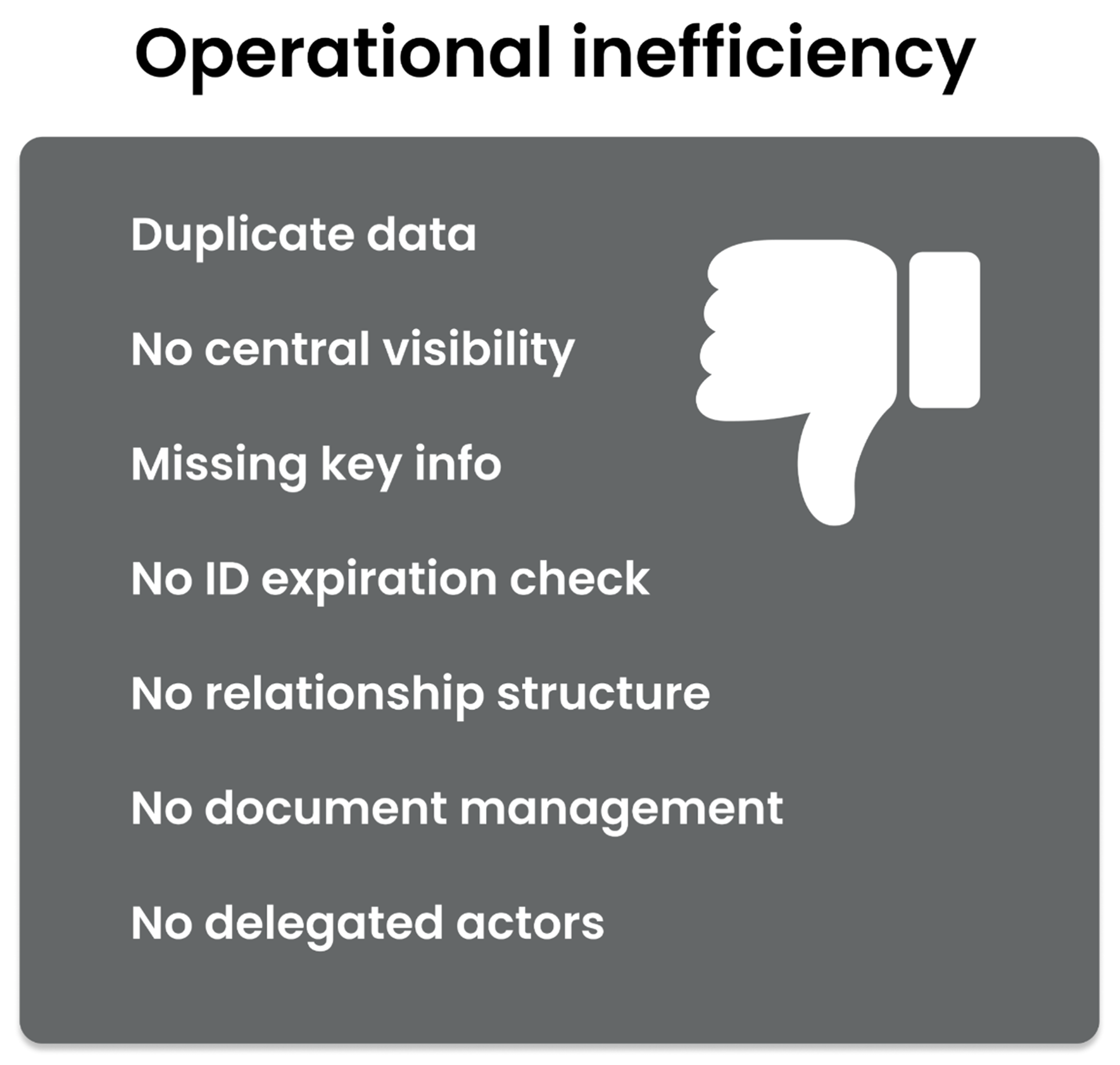
AI-powered identity risk management
- Automate identity proofing, background checks, and security validations
- Reduce unauthorized access by enforcing zero-trust security principles
- Detect and mitigate fraud with real-time identity analytics
Intelligent identity lifecycle management
- Seamlessly onboard, modify, and offboard third-party identities
- Customize workflows for vendor, partner, contractor and machine identity access
- Gain real-time visibility into identity activity and security threats
Privileged access management for compliance
- Enforce corporate and government security policies
- Ensure audit readiness with detailed tracking and reporting
- Reduce compliance risks with automated identity governance





