Managing Third-Party Identities in Microsoft Entra with idGenius
In most companies, there’s a well-defined process for managing employee identities and their access. Systems are usually integrated with HR, identities are traced from day one, and offboarding is linked to formal termination. However, the same can’t be said for third-party identities.
Partners, contractors, vendors, and third-party consultants often fall outside of the typical identity governance. They might be granted access through shared credentials or temporary accounts, where expiration dates aren’t clear and visibility is limited. These accounts can exist and remain active well beyond the end of the engagement.
Microsoft Entra is one solution that has strong access management capabilities for employees. But it's not built to address the scale, complexity, and diversity of non-employee identities.
That is where idGenius steps in. Designed to support third-party IAM and provide identity lifecycle management features, it complements Entra by tracking external users across departments, managing contract-based access, and providing audit-ready visibility. Together, these solutions enable companies to have greater control over each internal and external identity.
The third-party identity gap in modern environments
A shift in who needs access
The number of third-party users that require access to enterprise systems is growing at a fast rate. Among them are temporary workers, vendors, consultants, offshore teams, integration partners, managed service providers, and even automated agents belonging to external organizations.
Unlike your typical full-time employees, non-employee identities aren’t typically created through HR systems. They're not linked to onboarding checklists, and there usually isn't a centralized team responsible for their management. Ad-hoc access decisions are frequently made for non-employees, sometimes by business users without any IT involvement.
The hidden risk of external identities
These unmanaged accounts pose operational and security risks:
• Access tends to be excessive, granting more than what is necessary.
• Expirations are rarely enforced.
• Vendors that’re no longer involved may still retain valid credentials.
• There is no one who is responsible for the review processes.
And attackers are becoming increasingly aware of them. Third-party entry-point ransomware attacks rose 41% in 2025. Attackers commonly take advantage of poorly secured vendor credentials, unsecured VPNs, and software integrations.
Third-party IAM isn't just about provisioning access; it's about managing the whole identity life cycle. This includes onboarding with context, verifying access while in use, and revoking it once it’s no longer required.
Without centralized monitoring and policy-driven controls, organizations leave themselves with blind spots that are hard to see and even harder to resolve.
Microsoft Entra and the third-party gap
What Entra does well
Workforce identity management at scale
Microsoft Entra is a workforce identity and access management solution. It allows organizations to centralize authentication, enforce conditional access policies, and manage employee accounts for both cloud and on-premises apps.
Alignment with HR-driven processes
Entra delivers features like single sign-on (SSO), multi-factor authentication (MFA), and access reviews that enable IT departments to enforce compliance and internal security policies. All of these tools are most effective when tied back to an HR system, where identity records are structured and bound to official employee lifecycles.
Consistency across internal access
In this aspect, Entra excels. It helps organizations ensure that policies regarding provisioning and revoking access are applied, monitor risk signals, and manage privileges at scale. For companies looking to reduce overprovisioning for just their full-time employees, it's a great platform.
Where it falls short
Lack of support for non-employee workflows
The issues start when the user is not a typical employee. Third-party identities—contractors, vendors, brokers, or service accounts—do not typically follow the same lifecycle paths that employees do. Their inception may be requested by multiple business units, and they could be onboarded through ad-hoc workflows or assigned long-term access for short projects.
Visibility gaps and operational risk
Most companies can't answer, with certainty, who has access, why, and if it's still necessary. Not having a purpose-built framework to manage third-party identities and vendors makes it difficult to apply the same degree of governance to them as you would to internal users.
Built for the workforce, not the extended enterprise
Microsoft Entra wasn't built to account for the challenges that come with third-party identities. It offers the basic foundation, but for non-employee governance, that foundation must be built and expanded upon.
How idGenius enhances Microsoft Entra
Identity-centric third-party inventory
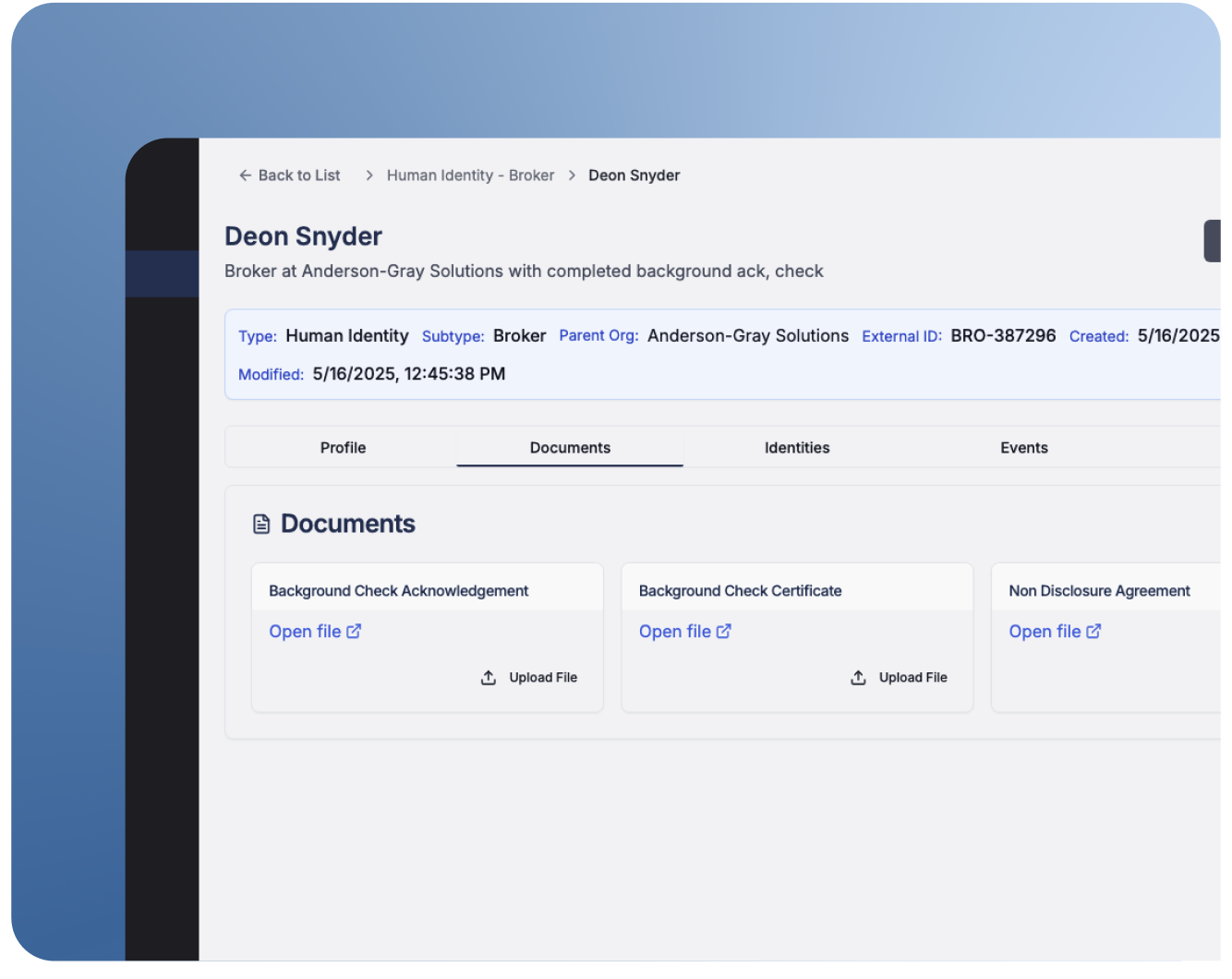
A unified view across departments
idGenius allows companies to bring order and structure to a typically overlooked area. As a platform, it acts as a centralized catalog of contractors, vendors, service accounts, and other external identities.
This catalog is more than just a list of accounts. Each identity is supported by context, with it being tied to:
• The sponsoring business unit.
• The assigned project or contract.
• A role, location, and verification status.
• Attached documents (e.g., NDAs, certificates)
Visibility across hybrid environments
While Entra focuses on accounts within Microsoft's environment, idGenius keeps track of identities across various systems. Whether third-party users receive access through Entra ID, external apps, or legacy systems, idGenius creates a single source of truth that is supported by historical context.
This allows security and operations teams to answer simple but important questions: Who is this identity? Why are they receiving access? What's the status of their contract?
Delegated identity management for business users
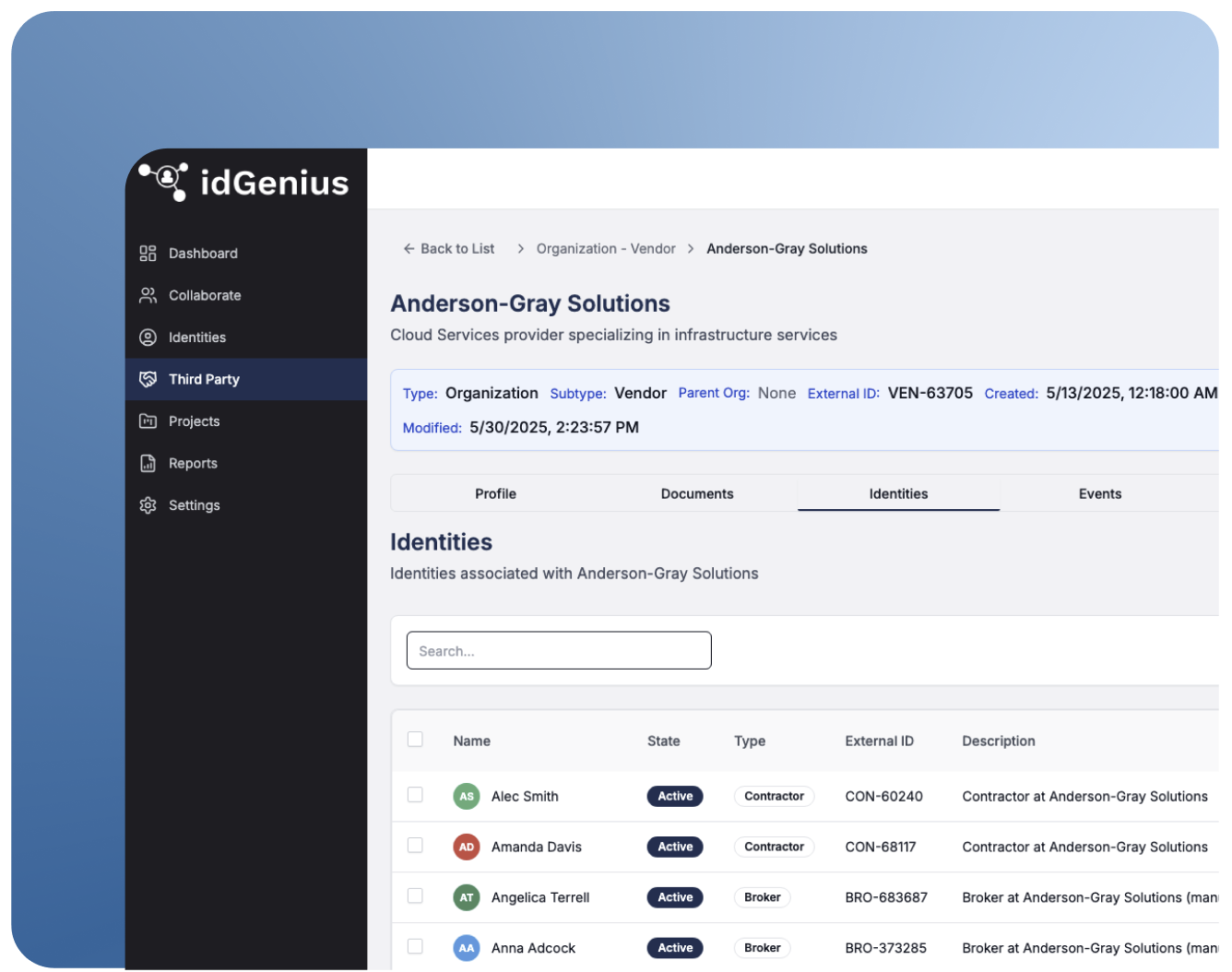
Governance beyond IT
In most organizations, IT teams may not be the ones who should manage access for third-party users. The reason for this being the fact that non-employee identities are often linked to projects or short-term initiatives that IT teams don’t have a full understanding of.
idGenius enables delegated governance through enabling relevant business users and vendor managers to:
• Approve or reject onboarding requests.
• Extend or renew access based on need.
• View historical access decisions.
This isn't the same as skipping over IT and operating behind them. This is delegating responsibility—with centralized control and auditability—to the people who know these identities best.
Lifecycle automation: Onboarding, expirations, and offboarding
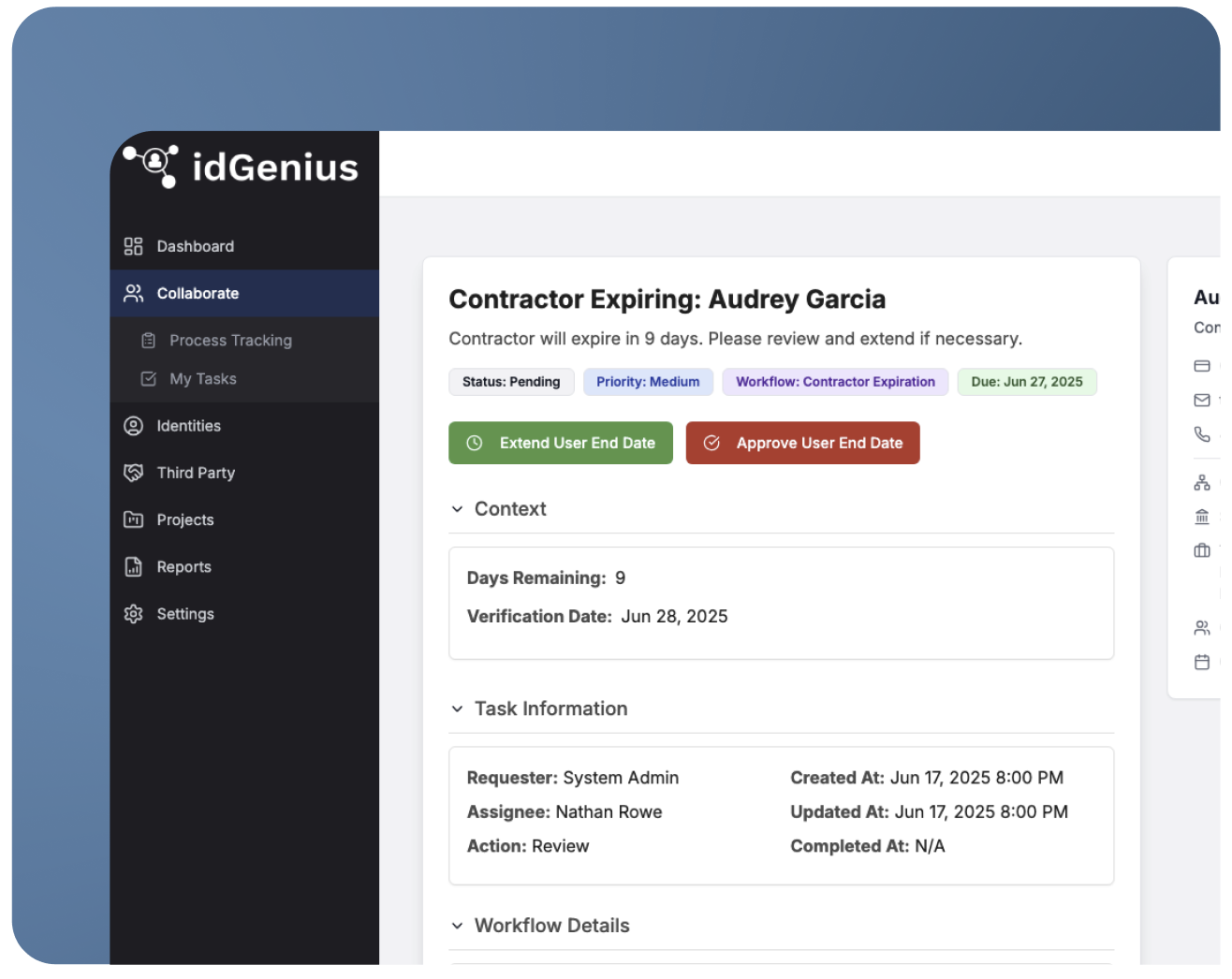
Manual offboarding creates gaps
Most organizations still rely on spreadsheets, ticketing tools, or emails to handle third-party identity lifecycles. Not only is a manual process slow and unreliable, but it can also create security risks as it can leave accounts active years after the contract has expired.
Automating the full identity lifecycle
idGenius introduces automation throughout key lifecycle stages:
• Onboarding: Triggered by requests that have been approved through idGenius’ built-in approval workflows. Onboarding is complete with verification checks, background screening, and a centralized location to upload and store any relevant documents.
• Expiration enforcement: Access is tied to project or contract duration, with optional review/renewal workflows.
• Offboarding: Automatic deprovisioning or notification when access is no longer justified.
This automation improves operational efficiency as well as reduces the security risks that can come from the existence of orphan accounts, overprivileged access, etc.
Compliance reporting and audit-ready history
Documentation tied to each identity
Regulatory compliance frameworks like HIPAA, ISO 27001, and SOC 2 demand that access be tied back to clear business need, bei documented, and can be revoked. For non-employee users, that means being able to prove things like:
• Who authorized the access
• What documents were signed
• When access began and ended
• What systems were accessed and why
idGenius stores this information at the identity level, as opposed to just at the account/vendor level. What this provides is the capability to easily satisfy audit requests without having to scour for information from disjointed systems.
Exportable, reviewable, traceable
Audit logs are exportable, reviewable, and shareable. Whether an organization is preparing for an external compliance audit or performing a review from within, all history is traceable.
Access events, approvals, expirations, and revocations are recorded in real time, allowing teams to document and review past intentions and actions.
Benefits of a combined solution
Microsoft Entra is designed for internal IAM. idGenius brings that same level of control to external users who may operate outside of traditional HR systems and processes.
Together, they create a more cohesive and inclusive solution to identity governance, one that includes full-time employees as well as the growing number of third-party users.
By combining the strengths of the two platforms, organizations can:
• Extend lifecycle management to all identities, bunot just internal.
• Allow business users to own and be responsible for the access they request.
• Eliminate orphaned or stale accounts with expiry and offboarding controls.
• Improve visibility into third-party risk in hybrid environments.
• Make reporting easier for internal teams and external audits.
• Identify and resolve security and compliance gaps that often fall under the radar.
Use case: Hybrid identity governance in action
Consider a multinational financial services firm that uses Microsoft Entra to manage access for its full-time employees. Their identities are tied to HR systems, governed by automated provisioning rules, and audited periodically. So far, so good…until third-party users enter the picture.
In order to enable growth and support regional initiatives, the organization begins engaging with external brokers and consultants, all across various business units. Access is handled differently within each region. Some create requests through IT, while others leverage implicit approvals. Expirations aren't handled the same, if they’re even being tracked. The number of external accounts builds up over time, and no one knows who still needs access and which accounts to retire.
In such a situation, pairing idGenius with Entra provides a more cohesive and unified solution to governance.
With idGenius in place, the organization would be able to:
• Maintain a centralized third-party user inventory, considering factors like vendor organization or project.
• Offload review duties to business users closest to the project.
• Automate renewal and expiration workflows based on contract lengths.
• Create audit logs tied to access history.
Similarly, they would be able to remove redundant third-party access, simplify audits, and reduce overall risk, all while ensuring their existing employee IAM infrastructure can function as normal.
How Anomalix & idGenius can help
Microsoft Entra is well-suited to handle internal identities. For third-party users, though, additional structure is needed, especially in terms of visibility, ownership, and lifecycle controls.
idGenius complements Entra by bringing identity-level context for non-employees, automated governance workflows, and policy-based expiration. For organizations that wish to get rid of any access gaps without fully redoing their existing systems, this combination offers a practical solution.
To learn more about how idGenius can help with third-party identity governance, reach out to us at info@anomalix.com.



