IAM consulting & implementation
Design, deploy, and optimize your identity ecosystem
From architecture to execution, our consulting and implementation services help you operationalize identity governance across your enterprise.
We work with your teams to configure scalable, secure IAM solutions—tailored to your infrastructure, users, and compliance requirements.

What we deliver

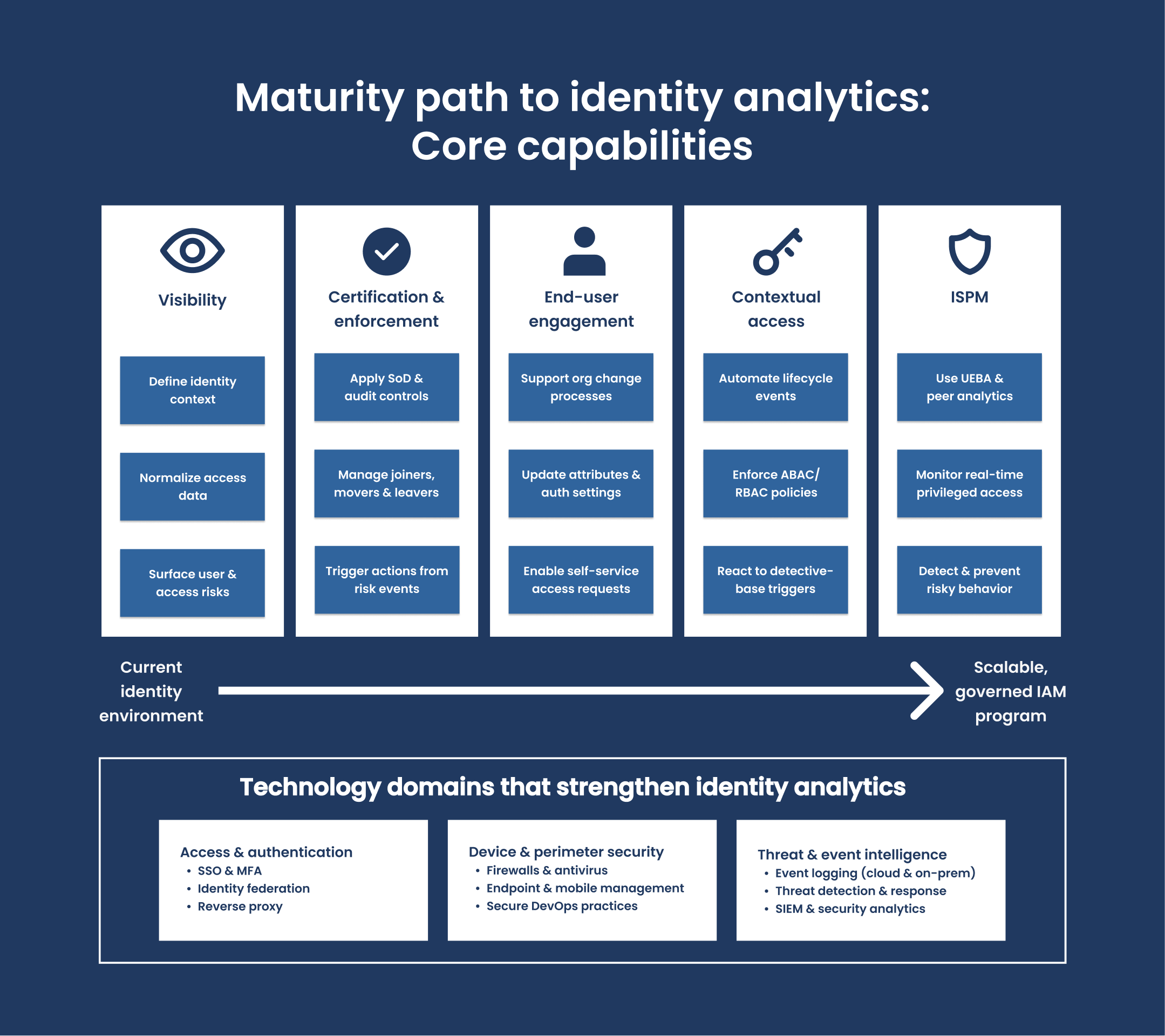
Identity governance and compliance assessments
We create custom architectures for cloud, hybrid, or on-prem environments—integrating seamlessly with HR, IT, and access systems to support your identity lifecycle.

Automated identity governance and administration
Implement automated workflows for provisioning, role-based access control, and deprovisioning. Improve efficiency, reduce human error, and enforce least-privilege access.

Privileged access
management
Deploy secure authentication methods that improve user experience and meet Zero Trust principles, including adaptive MFA, passwordless options, and identity federation.

Risk-based access controls and AI integration
Leverage behavior analytics and contextual data to enforce dynamic access policies, monitor threats, and respond to anomalies in real time.
Our approach
Our managed services are designed to flex with your organization’s scale, complexity, and compliance obligations.
You’ll gain access to identity experts, real-time insights, and responsive support without expanding your internal headcount.
24/7 monitoring and support

Regular reporting and review meetings

SLA-backed service delivery
Flexible support tiers and service models
How our clients benefit
A fully integrated IAM system ready for enterprise scale
Reduced time-to-value through automation and best practices
Improved access security and audit readiness
Enhanced user experience for employees, partners, and customers
A foundation for extending governance to third-party identities
Supporting your long-term identity success
Our implementation services are part of a broader identity journey. We partner with you from design to post-deployment support, and offer managed services to keep your IAM program secure, optimized, and up to date.



