idGenius & Secure Vendor Management
Executive summary
Operational complexity has made third-party vendors a central aspect of how companies do business and grow. Whilst these vendor relationships clearly have business advantages, they also give rise to a growing list of identity-based threats that traditional tools cannot handle.
Vendor Management Systems (VMS) are usually meant to manage contract terms and operational monitoring. They never, however, take into account the entire identity lifecycle of users from vendor organizations. This causes organizations to suffer from blind spots—like orphaned accounts, inconsistent offboarding, and visibility gaps—that accumulate and create vendor risk over time.
Secure vendor management requires more than just centralized contract management or documentation. It demands identity-first governance where vendors are not treated as just objects to track, but rather as sources of potentially high-risk access.
This white paper introduces a new vendor risk management strategy—one based on constant identity control, audit-ready processes, and sustainable risk mitigation. It outlines the ways that identity-first practices can support broader risk management goals while achieving regulatory compliance and reducing data breach risks related to third-party vendors.
By focusing on both the vendor firm itself and the identities it introduces into an organization, companies can build a basis for safe vendor management that adjusts toaone the complexity of modern vendor ecosystems.
The risks of unmanaged vendor organizations
Third-party vendors have become a key part of business operations, from cloud infrastructure to specialty consulting. However, every new vendor relationship does create a ripple effect—one that entails not just technical integrations but also further layers of identity exposure.
Beyond contracts: Identity gaps
Most vendor organizations bring their own users, systems, and service accounts into enterprise environments. Despite this, most businesses still treat vendor governance as a contractual requirement and not an identity governance problem.
Legacy vendor management processes concentrate on onboarding, cost analysis, vendor contracts, or something similar. What they usually lack is the capability to effectively support the provisioning, management, or deprovisioning of vendor identities across the vendor lifecycle. Third-party vendors can introduce dormant credentials, overly privileged access, and persistent system connections years after the completion of a project if the proper controls aren't in place.
The consequences of poor visibility
These blind spots create vendor risks that can't be solved with just checklists. Common failures include:
• Orphan or duplicate vendor accounts
• Access to systems outside of the authorized project scope
• Inconsistent vendor onboarding/offboarding processes
• Inadequate control of vendor identity hygiene
Why secure vendor management matters
Secure vendor management changes the focus from contract tracking to end-to-end governance of the lifecycle. It brings identity management into the fold of enterprise-wide risk management, allowing organizations to contain exposure while satisfying regulatory requirements. As vendor ecosystems grow more complex, identity-first control is essential—not just for security, but for long-term third-party risk management maturity.
The expanding scope of vendor-sourced identities
Vendors don't only bring services—they also bring identities
Every vendor organization comes with a mix of Its own external users, contractors, API keys, bots, and service accounts. More vendors mean the scope and complexity of the identity landscape also increases.
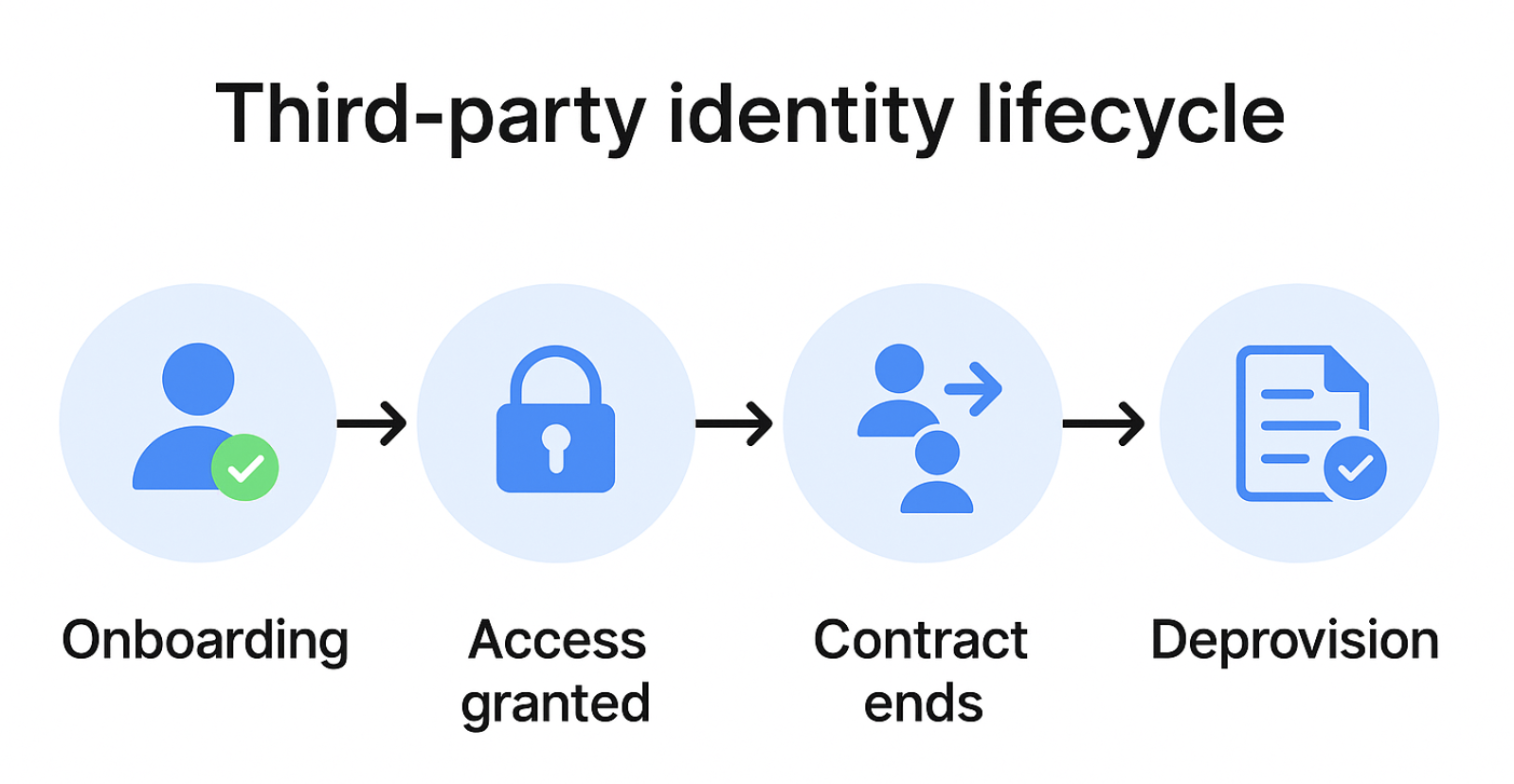
Vendor ecosystems are identity ecosystems
For each vendor contract in an organization, there may be multiple identities—human, non-human, automated, etc.—getting access to the environment. The issue here is that the majority of organizations continue to use manual provisioning, emails, or shared credentials to onboard and manage these users.
This can lead to an identity sprawl that doesn't originate from within the organization, but rather from third-party vendors and their varied internal procedures. Unstandardized onboarding processes and a lack of expiration policies make it difficult to manage and identify who still has access, and why.
Industry pressure is building
• In healthcare, vendors may have rotating clinical staff or temporary administrators with PHI access.
• In finance, external consultants may have close access to customer information and proprietary models.
• In manufacturing, equipment vendors often install agents or deploy APIs in production networks.
Though these are just a few examples, the risks extend well beyond just data breaches for most sectors. They can impact operational resilience, compliance, and vendor performance.
Why legacy approaches fall short
Spreadsheets for tracking vendors and simple access provisioning tools can't handle the scale needed to manage most third-party vendors. Without dedicated tools for secure vendor management, identity hygiene degrades as the number of third-party vendors goes up.
This is not just a user account problem—it is a governance problem that stems from how vendor relationships are formed and governed.
A governance solution must stay ahead of vendor identity complexity
To mitigate vendor risk, organizations need to transition from informal onboarding and offboarding practices to formal identity lifecycle controls. This includes:
• Assigning ownership of vendor-identities
• Tracking roles that are linked to specific contracts or projects
• Expiring access based on contract terms
• Reviewing vendor identity access periodically as part of ongoing risk assessment
These changes would allow companies to have a more solid foundation for vendor risk management—one that is more proportional to the scale of today's external identity ecosystems.
Why traditional VMS tools can’t deliver secure vendor management
Vendor management systems weren’t built for identity governance
Most Vendor Management Systems (VMS) were created to track contracts, onboarding documents, and payment terms. They help teams manage items related to procurement, vendor sourcing, and renewal cycles. They aren't usually designed to handle the identities that're being brought in by vendor organizations.
The ideal state is that once a vendor is "approved," their access will be manually granted, monitored, and taken away by internal teams. But as vendor ecosystems expand, this manual way is no longer feasible and secure.
What traditional VMS platforms miss
Typical VMS solutions lack features that directly support vendor security and compliance, creating systemic vendor risk:
• No visibility into how many identities a vendor organization introduces
• No expiration logic based on user role, project end date, or contract end date
• No native offboarding processes for vendors or user-level oversight of access
• No visibility into orphaned accounts when vendors leave
Real-world Impact
• 98% of organizations have at least one vendor that has experienced a data breach.
• In 2025, Coinbase suffered a data breach through a third-party support vendor, exposing customer records.
• Ascension Health disclosed a vendor-related breach that impacted hundreds of thousands of patient records due to outdated and unmanaged access.
Each of these incidents points to the same issue: vendor relationships were operationally approved, but the identity governance for it was missing.
VMS is not a secure vendor management tool
Vendor management systems are great at answering questions like:
• Is the vendor contract current?
• Has the required paperwork been submitted?
But they don't answer:
• Who exactly within the vendor organization has access?
• Is their access still required and properly bounded?
• Has access expired or been recently audited?
Why secure vendor management needs identity-first tools
As third-party vendors are more deeply embedded in business processes, organizations need more than simple contract management solutions. Secure vendor management requires a tool that supports:
• Role- and project-based provisioning
• Lifecycle-based deprovisioning
• Delegated identity entry and management by the vendor org
• Automated processes for vendor risk management that are linked to real-world activity
In order to reduce the frequency and impact of data breaches, organizations need to not rely on VMS tools to do the identity governance work as most simply doncompan't have the capabilities to effectively and efficiently do it.
Identity-first governance — a new standard for managing vendor relationships
Governance begins with accountability
With third-party vendors, the majority of companies can't answer one simple question: who is actually responsible for the relationship—not on paper, but in real life? Vendor relationships typically have poor identity-level visibility, and that leads to uneven access practices, vague accountability, and policy drift over time.
Identity-first governance shifts vendor management from just operational monitoring to security-oriented risk management. Instead of viewing vendors as abstract entities, it treats every vendor as a source of real users, systems, and credentials—each with potential identity implications and risk.
Core principles of identity-first governance
An identity-first strategy puts lifecycle awareness and control at its center. It makes sure vendor organizations and their users are monitored and audited continuously.
Key practices are:
• Delegating vendor identity governance activities to a business sponsor
• Relying on purpose-driven access based on certain roles or project needs
• Applying expiration rules based on contract terms or security policies
• Working with vendors to maintain and update identity lists
• Performing periodic risk checks to ensure access alignment
• This approach turns reactive vendor management into proactive risk management.
How it supports third-party risk management
Third-party risk management programs now examine not only the approval of vendor contracts, but also risk exposure downstream. This isn't just about knowing what a vendor is doing, but also knowing who they are doing it for, how they are getting into systems, and whether their permissions match their work scope.
Identity-first governance enables better vendor risk management through:
• Reduced over-permissioned accounts
• Improved audit readiness
• Better alignment with regulatory compliance goals
• Facilitating real-time access monitoring across the vendor lifecycle
A scalable foundation for secure vendor management
Effective onboarding is only one part of secure vendor management. It must be grounded in formal identity governance that is scalable with vendor complexity, adapts to organizational change, and facilitates sustained risk mitigation.
As an organization has more vendors, the potential expense of unmanaged identities increases exponentially. Without identity-first policies, even well-intentioned vendor relationships can introduce massive cybersecurity risks.
How idGenius enables secure vendor management
A no-code platform for identity-first vendor governance
idGenius is purpose-built specifically to help business users manage third-party vendors and the identities they introduce. Instead of adding access controls to outdated workflows, idGenius is an enterprise platform that treats vendors as identity sources with their own lifecycle, governance needs, and risk profiles.
With policy-enabled automation and delegated controls, it facilitates secure vendor management without additional administrative burden.
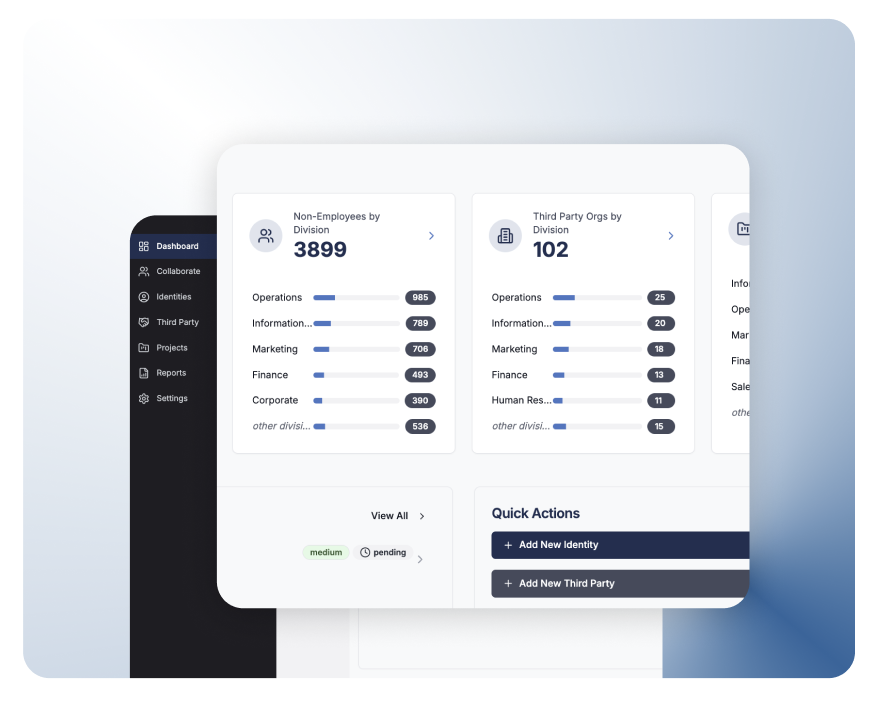
End-to-end governance across the vendor lifecycle
idGenius helps organizations manage every stage of the vendor identity lifecycle—from initial onboarding to final deprovisioning—with audit-ready tracking and built-in risk mitigation features.
idGenius helps companies manage every stage of the vendor identity lifecycle—from initial onboarding to final deprovisioning—through audit-ready monitoring and pre-integrated risk mitigation capabilities.
Here’s how it works across key lifecycle stages:

Delegated identity ownership by vendors
One of the largest vendor identity governance hurdles is maintaining accurate records. idGenius solves this by allowing vendor managers to be directly involved in the lifecycle processes. They can record, renew, and maintain their team members' identities on their own—within a company's defined guardrails. This reduces internal overhead whilst allowing data accuracy and accountability to be improved.
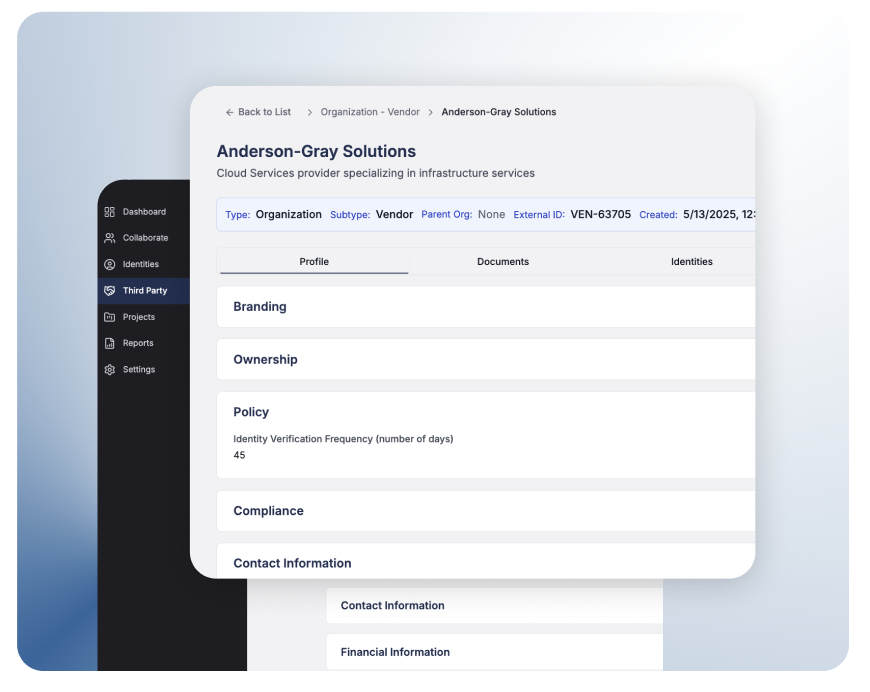
Alignment with security and compliance goals
By having a structured approach to vendor identity management, idGenius enables:
• ISO 27001-compliant access reviews
• Alignment with frameworks such as NIST 800-53, HITECH, and HIPAA
• Governance for Data Processing Agreements and vendor contracts
• Secure offboarding via audit documentation
• Compliance with company risk management plans
Real results, reduced exposure
With idGenius, organizations benefit from:
• Accelerated vendor onboarding procedures
• Fewer orphaned accounts
• Greater insight into vendor risk categories
• Streamlined access reviews and audit responses
• Better vendor performance by ensuring their identities have the access required when they need it
A smarter approach to secure vendor management
As vendor ecosystems grow more complex, so do the risks they bring. idGenius simplifies governance by making identity controls accessible, trackable, and scalable—delivering long-term protection without adding operational drag.
As vendor ecosystems become more complex, so do the risks they present. idGenius simplifies governance with identity capabilities that're accessible, auditable, and scalable—providing long-term security without the added complexity.
VMS vs. identity governance
Not all vendor management tools are built for security
Vendor management systems do have a purpose—but mainly for operational tasks. Most VMS tools weren't designed to support identity lifecycle needs, often leaving critical risk management tasks unaddressed. This shortfall can expose organizations to security threats that things like compliance tools can't protect from.
Side-by-side: operational vs. identity-first capabilities
The table below compares a typical vendor management system solution with an identity-first platform like idGenius.

Why identity governance delivers better risk outcomes
Typical VMS solutions may be able to help with things like vendor selection and contract management. But for organizations that want true control over third-party vendors, these platforms fall short. Identity-first solutions seal the gaps that lead to security breaches and lay the foundation for effective third-party risk management and risk mitigation.
How a vendor with orphaned accounts can cause a breach
Though the exact details vary from case to case, orphaned accounts and access have often led to data breaches with significant damage. Detailed below is one potential way that such an event can occur:
When a vendor leaves, but their access remains
A company ends its brief engagement with a third-party vendor to support a regional rollout initiative. At the project's closure, the contract was marked "complete" in their VMS. Within the company, the relationship was considered closed.
What individuals did not realize was that a few service accounts and administrative logins had been established by the vendor during the engagement. None of these were closed down following the vendor off-boarding process. Several months later, the same vendor was hired once more—this time by a different business unit. A new set of credentials were created, but the previous ones were never deleted.
A failure of process, not intent
The breach occurred when a compromised account from the initial project was used to access an internal database that had no MFA configured and had not been reviewed for six months. By the time the breach was observed, customer data had been exfiltrated.
This was not a tools failure—it was an identity governance failure. The VMS flagged the vendor as inactive, yet there had not been an appropriate identity review performed. There was no risk assessment tied to the technical footprint of the vendor, and no incident response plan that included a credential inventory of vendors who were retired.
What should have happened instead
By having a secure vendor management process, the vendor's access and identities should have expired and been removed at the contract's end. Role assignments would have been monitored and a scheduled offboarding workflow would have removed unused credentials.
Conclusion & next steps
Secure vendor management is not just a checklist, it's an ongoing responsibility that spans identity governance, risk mitigation, and vendor accountability, supported by the correct platform. As the number and complexity of vendor relationships increase, organizations can no longer rely on spreadsheets, contracts, or outdated Vendor Management Systems to mitigate risk.
Effective vendor risk management means companies have visibility into the identities each vendor organization brings with them, how and why they are being used, and whether they are still needed. This is not just provisioning, it is adding risk assessment and control throughout the vendor lifecycle.
Identity-first strategies offer a path to scale. By connecting vendor onboarding, access reviews, and deprovisioning to overall third-party risk management goals, companies reduce the risk of data breaches and improve their overall security posture.
idGenius is a solution that allows teams to realize this vision—providing tools for continuous monitoring, delegated identity management, automated offboarding, and audit-ready reporting.
It is time to rethink vendor relationship management. Contact info@anomalix.com to get started on your journey today.
Mohammed Elkhatib is Founder and CEO at Anomalix. Prior to founding Anomalix, Mohammed led global operations for Aveksa (acquired by RSA) where he was responsible for Sales, PreSales, Engineering and Professional Services. Mohammed is an Identity Security expert with over 25 years of IT and Business experience.



