Third-Party/Non-Employee Identity Governance for RSA Governance and Lifecycle
Identity governance is only as strong as its scope
RSA Governance & Lifecycle is a product that is widely used solution for employee access governance. It assists companies with establishing access visibility as well as conducting access reviews, policy enforcement, auto-provisioning, audit and compliance for systems, applications, and data. Nevertheless, it wasn't made specifically for the growing group of users who fall outside the boundaries of conventional employment.
The modern workforce now comprises of non-human and third-party identities such as contractors, vendors, brokers, partners, service accounts, machine workloads and API integrations—identities that don't typically reside in core HR systems. These users (and things) also need access to sensitive information, internal systems, and project workspaces. Over time, it becomes challenging to manage these identities without tools specifically designed for them, causing friction and putting organizations at risk.
idGenius fills that void. It works in conjunction with RSA and other Identity Governance Administration (IGA) systems, supplying third-party identity context and lifecycle management that the IGA platforms don't usually possess. Combined, the systems bring accountability to identities that have traditionally been overlooked.
This blog explores how idGenius augments and extends RSA Governance & Lifecycle for the organizations that need to track, certify, and govern access for non-employee identities at scale.
Why RSA IGA could be made even better
Traditional tools weren’t designed for external users
RSA Governance & Lifecycle and most identity governance tools were designed for employees. It provides very structured workflows for internal personnel but often lacks visibility into identities that don't go through the standard HR onboarding channels. IGA systems typically rely on a trusted source of truth for Identities that originate in an HR system. The lifecycle events of the identity, such as Joiner, Mover and Leaver, come from an HR system that is then consumed by an IGA system.
Manual processes lead to visibility issues
Non-employees—contractors, vendors, third-party service providers, etc.—usually enter internal systems via ad hoc processes. Their identities might be stored in spreadsheets, in ticketing systems, an email, or not even recorded at all. This makes it difficult to assign ownership, impose access policies, manage lifecycle events, or maintain a clear audit trail.
The consequence: Access governance gaps
Without identity-first control, third-party accounts are likely to fall between the cracks of your typical reviews. They may be granted too much access, stay active long after their engagement has expired, or be assigned no sponsor/owner. Such weaknesses expose organizations to risk.
RSA is excellent at controlling what it sees. The challenge is that it often doesn’t see enough. That's where idGenius steps in, helping organizations govern external identities before they reach the IGA layer.
How idGenius fits into your existing IGA stack
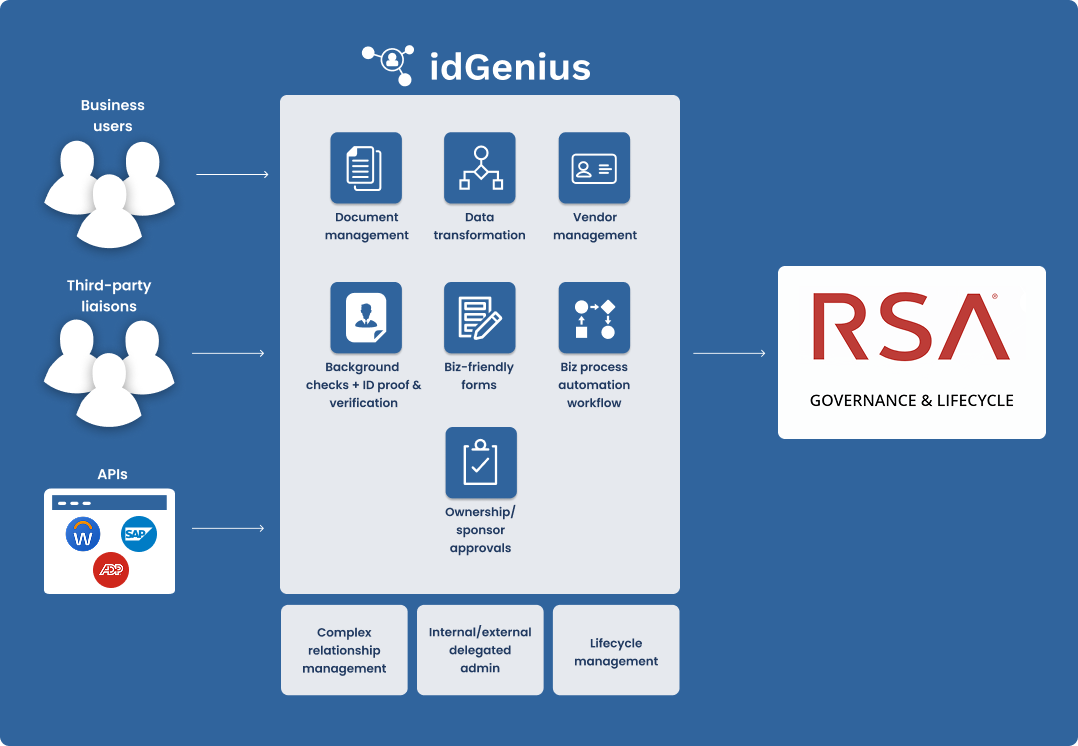
Purpose-built identity context for RSA
idGenius works alongside RSA, not instead of it. It serves as the system of record for non-employee identities and their associated third-party organizations before flowing into downstream systems.
It maintains vital identity attributes not inherent in RSA straight out-of-the-box: identity owners and sponsors responsible for approvals, project affiliation, contract terms, expiration dates, and all required documents. These data points help ensure that there’s accountability early in the identity lifecycle and consistent governance throughout.
Automated onboarding and project-based controls
For example, when hiring a contractor, idGenius will be able to automatically:
• Order background checks, credit checks, and identity verification.
• Request access that would not be granted in birth-right roles or based on high-risk project roles.
• Request access that would not be granted in birth-right roles or based on high-risk project roles.
• Issue expiration and renewal workflows aligned with contract terms.
• Capture performance history feedback.
All of this context is organized, auditable, and ready for consumption for RSA workflows.
Reducing manual overhead
Manual processes are one of the main causes for governance breakdown, yet studies show that 96% of organizations still rely on manual workflows in their organizations. With idGenius, third-party identity onboarding and upkeep become much more structured and simpler to audit. It’s no longer a manual process.
RSA remains responsible for things like authenticating access, establishing access visibility, automating provisioning, and enforcing SoD controls. idGenius simply makes sure that the identities entering those processes are adequately-scoped, adequately-sponsored, and adequately-tracked from the beginning.
Access reviews for third-party users in RSA

Why non-employee access reviews fall short
Access reviews are only as effective and useful as the context behind them. RSA Governance & Lifecycle is able to automate and provide certifications, but it will often not have the necessary details to make decisions on non-employee identities.
idGenius fills in that gap by adding another level of clarity. It attributes every identity to a specific sponsor, project, contract term, and ultimately, an expiration date. This means that access review decisions aren’t made based on guesswork, but rather, they can be made by the business users who actually know what the identity is for and if it’s still valid based on business decisions.
Context-aware reviews through idGenius
With idGenius giving RSA informed context, organizations can:
• Provide certifications to business sponsors, not just IT
• Include project metadata, contract expiration dates, and role details in the review request
• Make decisions like approving, rejecting, or extending without changing tools
• Automate reviews based on real-world events (like contract expiration), not calendar periods
This type of automation helps focus attention on the things that truly matter.
Addressing privilege creep with real insight
It also prevents a well-documented threat: privilege creep. A study found that 82% of organizations granted highly privileged cloud positions to third-party providers, unbeknownst to security teams. With idGenius connected to RSA, access decisions can be made with context-aware visibility into the scope and reason for every permission.
The result is a more accurate and auditable certification process for non-employee identities that doesn’t cause friction in existing RSA processes.
Preventing orphaned accounts and SoD violations in hybrid environments

Access doesn’t always end when contracts do
Access isn’t always removed when a contract ends—though it should be. Even if a supplier is marked "inactive" within a VMS, their accounts in other connected systems can remain open. RSA can enforce policies, but only if it knows an identity exists and what it's tied to.
Automated lifecycle triggers prevent dormant access
idGenius keeps access from lingering once it is no longer required by implementing expiration and renewal workflows at the identity level. Every third-party identity in the system has an end date, sponsor, and access scope—giving RSA the framework it needs to act with confidence.
These workflows reduce the risk of orphaned accounts, which is still a very real threat. More than half (54%) of organizations have experienced a breach that can be traced back to third-party access. When identities outside of the organization stay active once they're no longer involved, they become an open door.
Surfacing SoD conflicts and audit exposure
idGenius also provides simpler way to detect and react to SoD violations against external users. For instance, there may be a conflict if a contractor is involved in two distinct, high-privilege projects. Without centralized monitoring, these instances can go unnoticed.
Research has shown that 89% of organizations identified third-party access-related audit findings that they couldn’t quickly remediate. By revealing duplicate access and making expiration reviews easier, idGenius gives RSA the visibility it needs to enforce SoD policies and address stale or risky access—before it becomes an incident.
What organizations gain by using idGenius with RSA
Empowering business sponsors and simplifying access
With RSA and idGenius together, organizations don't just receive process improvements—they receive better control, faster decisions, and fewer gaps in oversight.
Business sponsors can manage their own third-party users without depending on IT teams. Identity checks become more explicit and faster, as each identity has context that is relevant like project, length, and role.
Faster onboarding with less friction
Onboarding identities is faster as well. idGenius provides pre-designed, no-code forms that capture required information once. Identity verification, background checks, and documentation all occur in one place. Less back-and-forth emails and faster time to initial access are just a few of the benefits idGenius powers.
Improved compliance standpoint
From an audit perspective, idGenius’ value is also visible. idGenius keeps a full record of historical changes made across onboarding, renewals, document uploads, and access certifications. It's all audit-ready and correctly mapped to the correct identity from inception to completion.
There's a real cost savings as well. Third-party breaches are about 40% more costly to fix than internal ones. Preventing just one breach—by ensuring a vendor's access is cut off on time or a conflict is raised early—can offset months of governance effort.
RSA and idGenius combined allow organizations to reduce friction, close governance gaps, and have non-employee identities exist in accordance with policy.
Better together—idGenius and RSA for non-employee identity governance
RSA Governance & Lifecycle is still a key part of access control in many organizations. It handles certifications, SoD enforcement, and compliance reporting at scale. But when third-party identities are brought into the equation, traditional IGA tools fall short.
idGenius fills that gap. It adds structure, transparency, and lifecycle management of non-employees and third-party identities before their introduction into RSA workflows. With access based on projects, sponsor responsibility, and automated reviews, organizations can make more informed access decisions without additional administrative overhead.
This combined approach is becoming more and more necessary. With non-employees representing nearly half of active identities and third-party breaches escalating, governance models must adapt.
RSA provides the enforcement. idGenius supplies the context.
How Anomalix can help you govern third-party identities with RSA
Identity governance isn’t complete without visibility into non-employee access. idGenius brings that missing context to RSA Governance & Lifecycle—enabling organizations to manage external identities with the same level of oversight as full-time employees.
From onboarding through offboarding, idGenius helps track sponsorship, enforce expiration workflows, and automate reviews across your hybrid environment.
Want to see how it works in your environment? Contact us at info@anomalix.com to schedule a tailored demo or see how idGenius works alongside RSA to simplify third-party identity governance and reduce access risk.



