Anomalix Enables Secure Office 365 Access
Anomalix helps organizations achieve visibility and control over business and compliance-sensitive resources for the entire enterprise user base. This grants insight into user access and a holistic pathway to ensure that proper access is available to the right people at the right time and in an auditable fashion.
Identity Context and Access Governance Controls
Anomalix helps organizations achieve visibility and control over business and compliance-sensitive resources for the entire enterprise user base. This grants insight into user access and a holistic pathway to ensure that proper access is available to the right people at the right time and in an auditable fashion.
Anomalix’s Access Governance solutions enable enterprises to answer Audit and Security Questions such as:
- “Who has access to what?”
- “Which users and access are considered privileged and high risk?”
- “Should this user have access?”
- “How did they get that access?”
- “Does the user access violate corporate or compliance-based policies?”
- “Is this user who they say they are?”
- “How does a user’s access profile compare to their peer group?”
- “Is this user’s behavior anomalous?”
Audit requirements are typically addressed by providing ways to review the state of access at various organizational levels – from company-wide to first line managers. Additionally, the most common use cases revolve around ensuring that new hires, terminations and changing roles within the enterprise can be handled using access requests and provisioning capabilities. Anomalix’s expertise is helping organizations realize increases in efficiency when dealing with auditors, reducing costs associated with the certification cycle, and creating a sustainable model for ongoing audit compliance.
Visibility, Security and Compliance Beyond Office 365
Traditional on-premise Active Directory deployments have been proven to be a treasure trove of security and compliance-relevant information. With the widespread adoption of Azure, organizations are now facing previously unforeseen challenges around user access controls and user license assignments. These emerging issues require Security, Risk and Compliance perspectives that organizations are grappling with. Establishing Access Visibility, Contextual Control and Approval-based Access Automation for on-premise and cloud resources are key struggles in modern hybrid environments.
Microsoft’s Office 365 is the modern packaging of its classic set of offerings for the enterprise – Microsoft Office Suite, Exchange, Lync and SharePoint. It provides a path for enterprises to migrate everything to the cloud while providing tools to maintain a hybrid infrastructure for all or some of the offerings.
Visibility, Control and Audit Readiness
The establishment of an access governance program requires a number of foundational activities to be truly effective. Mature organizations must consider the following when planning for a modern IAG implementation:
- Establish identity context – modeling what the various types of identities will contain at an attribute level and what authoritative sources of information must be consumed
- Gain access visibility– determine how to obtain identity, account and entitlement information. This is essential to establish the “Who has access to What?” baseline
- Inject business policies, security mandates, and audit controls – translate business processes around compliance, audit, and segregation of duties an access governance system to enforce changes required as a result of reviews or explicit requests. This will reduce day-to-day operational tasks allowing administrators to focus on critical enterprise needs
- Enable end-user access request processes – empower users to request and maintain non-standard access while ensuring that access is appropriate through risk-based approvals
- Automate access provisioning and de-provisioning – drive organizational efficiencies and reduce the risk of incorrect or unapproved access from being given via direct provisioning integrations to target systems
- Audit Readiness – through a combination of security and compliance reviews, reports, and metrics, rely on automated processes and delegated authority to
- User and Entity Behavior Analytics – utilize advanced analytics and machine learning techniques to identify previously undiscovered commonalities in user access, detect anomalous behavior not evident in standard access patterns, and take action against events that signify unauthorized user behavior
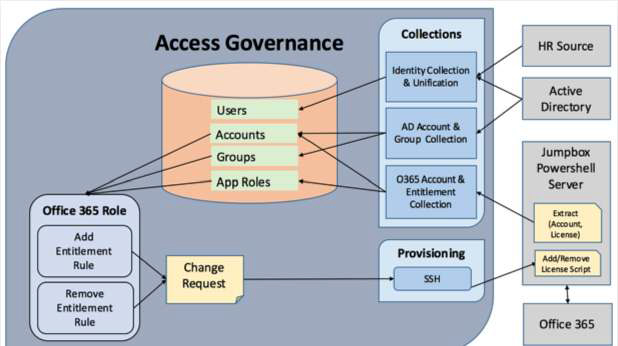
Bringing O365 under the Access Governance Umbrella
The most effective way to integrate O365 access visibility, controls, and provisioning is to leverage Microsoft’s PowerShell APIs. These provide granular access to all licensing and access control functionality as well as enabling “pull and push” data management. Anomalix has developed proprietary capabilities that allow enterprises to integrate O365 with their IAG environment.
Mohammed Elkhatib is Founder and CEO at Anomalix. Prior to founding Anomalix, Mohammed led global operations for Aveksa (acquired by RSA) where he was responsible for Sales, PreSales, Engineering and Professional Services. Mohammed is an Identity Security expert with over 25 years of IT and Business experience.



