Third-Party Identity Management: 2025 Compliance Guide for CISOs
As identity systems expand to include non-employee users—partners, contractors, brokers, APIs—the security and compliance risks are increasing. These identities usually exist outside of standard HR systems, yet they still need to have access to business assets, internal systems, and sensitive data.
Most organizations have yet to make their access management models conform to this shift. Typical Identity and Access Management (IAM) products focus largely on full-time employees. Therefore, third-party identities fall through the cracks, and causing monitoring and accountability gaps to be created.
Regulatory agencies have begun to take notice. In recent times, regulations around transparency, breach reporting, and vendor risk management requirements have become stricter, and it doesn't look like it'll loosen up anytime soon. Identity governance should be treated as mandatory in the case of external access—especially when third-party risk is playing a bigger role in high-impact data breaches these days.
For CISOs, security professionals, and compliance personnel, the challenge is clear: align identity management processes with regulatory mandates, whilst maintaining continuous visibility and control for all user identities—both internal and external.
Why regulatory pressure is rising
As more data breach events are traced back to third-parties, regulators are holding companies responsible for who is permitted access, as opposed to just holding them accountable for how their systems are protected. In essence, companies are required to prove third-party identities are handled with the same precision as their standard employee.
With this, organizations are now rethinking how identity governance and vendor risk management may overlap. They're abandoning ad hoc methods and heading towards identity management practices that support regulatory compliance, access certification, and incident responses.
Manual reviews and basic tools no longer cut it. Scalability, auditability, and control are now a bare minimum for external access management.
The compliance risk of third-party identities
More often than not, third-party access is invisible, unmanaged, or unacknowledged. That uncertainty leads to breakdowns in compliance. More than 60% of organizations saw a third-party breach—a nearly 50% jump from the previous year. When access is provided to external users without the proper governance, it's hard to pinpoint what exactly went wrong until it's much too late.
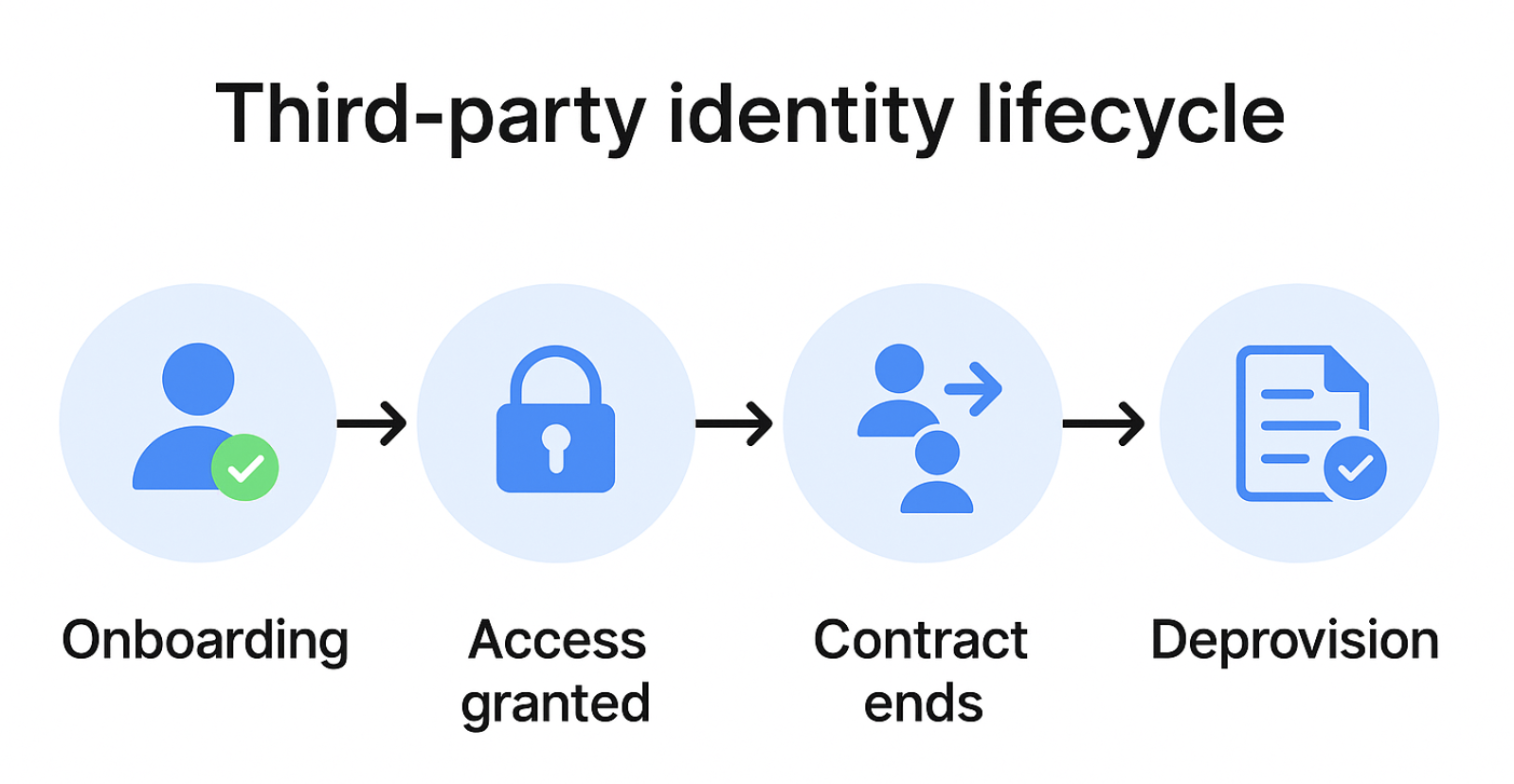
Third-party breaches aren't solely caused by malware and phishing. How access is being granted and managed often plays a part in it as well:
· Credentials shared across departments
· Never audited or revoked service accounts
· Contractor access still granted months following departure
· No expiration or renewal policy in place
· Privileges granted without adequate reason
These failures don't necessarily trigger alarms, but they tend to appear during audits or incident response investigations. Third-party breaches are costlier, as well: Gartner estimates that remediating a third-party breach costs up to 40% more than a standard data breach due to the complexity of managing external relationships and expanded impact.
Risk grows when third parties are treated as isolated exceptions, creating identity security blind spots. In reality, partners, vendors, and contractors may outnumber internal users, especially in SaaS applications or shared environments. Without adequate for lifecycle management in place, organizations have no guaranteed way of knowing when to shut down access—or even who approved it.
Key regulations impacting non-employee access
Although past cybersecurity regulations focused on internal systems and data protection, modern expectations now include external-facing users, vendors, and contractors who have access to business assets or sensitive data.
Several federal regulations and regulatory bodies have introduced new regulations or methods of enforcement that directly affect the manner in which non-employee identities need to be handled.
SEC cybersecurity disclosure rule
The Securities and Exchange Commission (SEC) requires material cybersecurity breaches to be disclosed by public companies within four business days using Form 8-K. This includes breaches through third parties such as vendors, contractors, or cloud providers.
The rule also requires companies to make the following disclosures:
· Governance structures for managing cyber risks
· Risk management processes, including processes involving third-party access
· The board's involvement with security practices
A disclosure is also needed for a violation involving a contractor if operations, customers, or investors are affected. Not disclosing such details can result in shareholder litigation or enforcement from the regulators.
HIPAA and business associate agreements
Health care providers are held accountable for third-party vendors' access to and handling of patient data. HIPAA mandates that covered entities have business associate agreements (BAAs) with vendors that create, receive, or transmit protected health information (PHI) on behalf of the covered entity.
Regulators expect:
· Identity proofing for third-party access
· Least privilege enforcement for all vendor accounts
· Immediate breach reporting from the vendor to the covered entity
In the last few years, lapses and failures in third-party access management have resulted in million dollar fines.
FINRA oversight and enforcement
For FINRA-regulated financial institutions, third-party vendor identity governance is turning into an area commonly focused on during audits. FINRA has cautioned firms for not terminating access at contract expiration, not maintaining inventories of third-party accounts, and not having a proper incident response coordination with third-parties.
Inspectors want to see:
· Clear offboarding procedures for non-employees
· Documentation for how/why third-party access was granted
· Proof of regular access reviews and expiration settings
What CISOs must track to stay audit-ready
To be compliant, CISOs must focus on identity-specific logs that validate control over external users. The logs must be centralized, audit-friendly, and updated.
Here are some key categories to document:
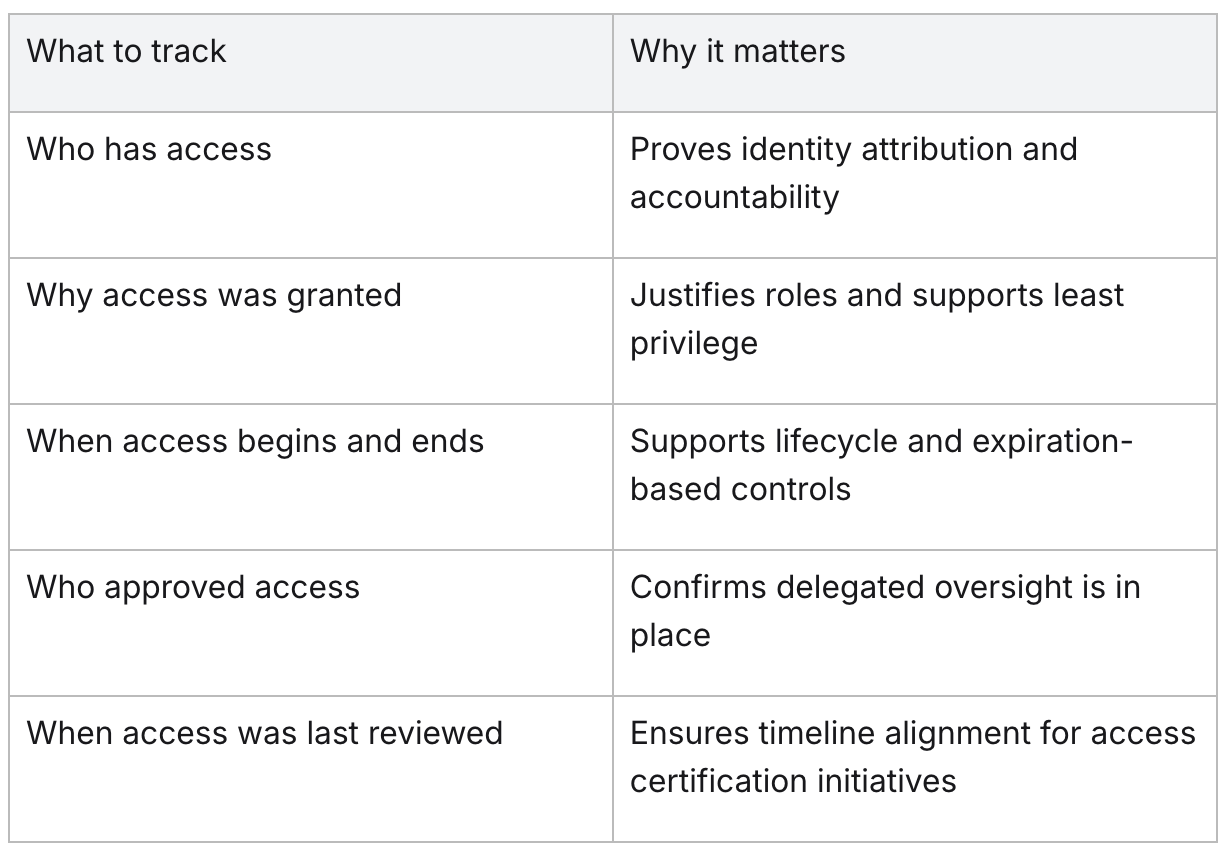
In addition to documentation, real-time visibility is essential to have as well. If a vendor account remains active after the contract ends—or if there are many roles left unreviewed—auditors may label it as an access governance failure.
Automated alerts, centralized audit logs, and platform-based certification workflows can help enable continuous compliance. But these tools are only as useful as the policies that support it. This means that it's critical for identity governance policies to explicitly outline who is responsible for approving, revoking, and monitoring access.
Designing a compliance-aligned governance strategy
A strong third-party user identity governance strategy begins with process, not technology. Software and tools might facilitate compliance, but it cannot compensate for unclear roles, inconsistent approvals, or missing lifecycle events.
Third-party identities typically do not follow HR-driven workflows. That means IT and business stakeholders must agree on shared responsibilities for access decisions, documentation, and offboarding. In the absence of this alignment, privileged access will linger indefinitely or be issued out of context.
In order to enable compliance and reduce exposure, organizations need:
· Project-based provisioning time windows in line with contractual terms
· Role-based access rules implemented during onboarding
· Automated expirations with review or renewal checkpoints
· Delegated access management for departments or project leads
· Centralized documentation of approval chains
These policies must be applied to all digital identities, not just employees. The least privilege principle should be the guide for every access decision.
By associating identity decisions with business rules and contractual terms, organizations can reduce administrative effort and improve regulatory compliance. A policy-based, documented process also serves as the foundation for audit readiness, access review, and risk-based access control across the third-party ecosystem.
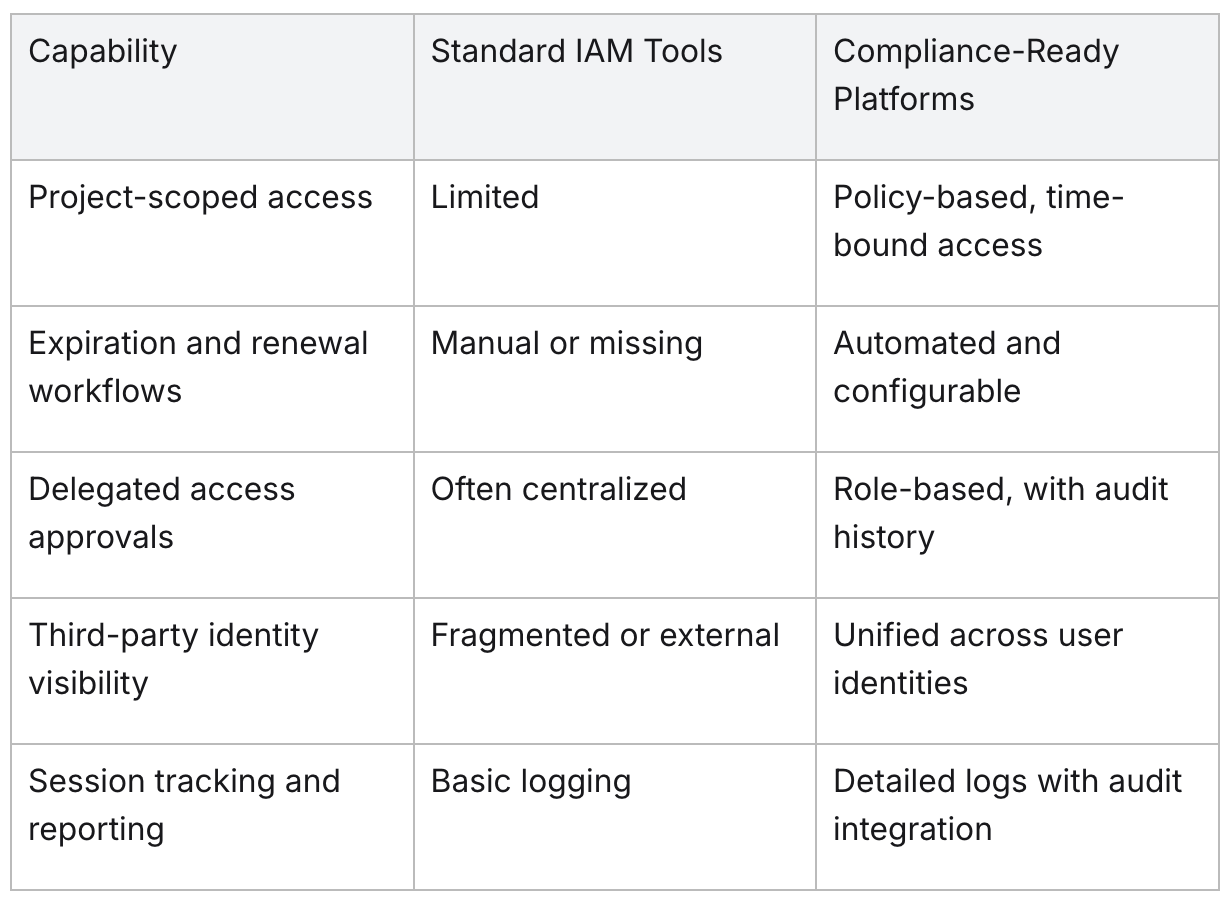
Technology capabilities that support compliance
Even well-defined access policies can fail without the right tools to implement them. The majority of identity and access management platforms were designed with employees in mind and are therefore not adapted to manage third-party identities at scale.
The following table outlines where legacy IAM platforms fall short—and what's needed for compliance-driven third-party access management:
An identity platform with external access control, session management, and delegated access workflows helps to enforce accountability during the third-party lifecycle. It also helps with business continuity by reducing onboarding friction and streamlining the access review processes.
Learn more about how idGenius can support the capabilities listed above—and more.
Final thoughts + CISO action checklist
Third-party identities are at the heart of today's business operations, yet they're also one of the least governed areas of identity security. With growing regulatory pressures, manual processes and local identity stores aren't sufficient.
For CISOs, this means integrating identity management into every stage of the third-party lifecycle.
Here's a quick checklist to ensure audit and compliance readiness:
· Inventory all third-party and digital identities
· Assign roles based on project scope, not job title
· Automate expirations and apply access controls
· Require multi-factor authentication for all external access
· Monitor all delegated access decisions and approvals
· Align governance with the applicable U.S. regulations (e.g., SEC, HIPAA, FINRA)
How Anomalix can help you govern third-party identities
Managing third-party identities requires more than extending internal IAM tools. Organizations need a purpose-built solution that accounts for non-employee workflows, project-based access, and compliance-driven governance; a solution like idGenius.
Anomalix helps organizations automate external identity lifecycle management, enforce policy-based access, and maintain audit-ready records—without adding operational overhead.
Have questions about third-party identity management or want to learn more about idGenius? Contact us at info@anomalix.com to see how we can help.
Mohammed Elkhatib is Founder and CEO at Anomalix. Prior to founding Anomalix, Mohammed led global operations for Aveksa (acquired by RSA) where he was responsible for Sales, PreSales, Engineering and Professional Services. Mohammed is an Identity Security expert with over 25 years of IT and Business experience.



