Manage Non-Employee Identities at Scale with idGenius
Executive summary
Organizations rely on a wide range of external partners, whether it be contractors, suppliers, service providers, or temporary workers. All these non-employee identities require varying levels of access to internal systems and are now a large component of most organizations, regardless of industry.
Unlike your typical employees, non-employees are often linked to specific projects, contracts, or deliverables. Their access needs are temporary and at times, unpredictable. Managing these identities and access rights manually often introduces additional risks to operations and security.
Non-employee governance refers to the processes, workflows, and procedures used to manage identities beyond the permanent workforce. It covers anything from how third-party user onboarding occurs, how access is granted and revoked, and even how internal systems for these identities are maintained.
The issue is that traditional Identity and Access Management (IAM) products weren’t built for these third-party identities. They are typically designed to handle full-time employees and would struggle to adjust to external user needs. This leads to gaps appearing, especially in key processes such as approval tracking, audit trails, or timely deprovisioning.
These gaps can lead to issues that affect more than just the IT department. Regulators focus more and more on the management of third-party access. In many sectors, a failure to demonstrate good management of non-employee identities can potentially lead to audit problems or even a breach.
This whitepaper addresses the danger of unmanaged external access and outlines how a purpose-built approach to third-party identity governance can address those issues. It also introduces idGenius, a platform that has the ability to support organizations with non-employee governance at scale.
Understanding non-employee identities
Who works beyond the employee perimeter?
Non-employee identities are entities and organizations that work outside a company's workforce but need to have access to internal systems. They usually include:
• Contractors and consultants
• Vendors and suppliers
• Channel partners and affiliates
• Temporary workers and interns
• Outsourced teams and managed service providers
• Robotic process automation (RPA) bots or machine identities on behalf of third-parties
They frequently access sensitive applications, cloud environments, or operational data. Their access is necessary for the business to function but is typically controlled in an informal manner.
The governance challenge
Non-employee users are not usually tracked in HR systems. Their point of entry within the company can vary, procurement, legal, operations, IT, etc. As a result, their identity lifecycle is rarely centralized or synchronized with existing IAM systems.
Most organizations lack an accurate headcount of their non-employee users. Even fewer have a clear understanding of the systems they have access to, or the duration of said access. Such limited visibility makes simple tasks like regular access reviews, deprovisioning, and compliance audits challenging.
Why they require a unique solution
Non-employee identities have distinct governance requirements in a number of important ways:
• Access is often project- or contract-based
• Approvals may be from business units rather than HR
• Access needs can change mid-engagement
• Users can be from external firms with their own policies and hierarchies
Conventional employee provisioning software depends on static associations and HR requests. Not all of these assumptions apply to third-party users as well. A solution that manages third-party users should support/streamline variable start and end dates, forms of access, and fragmented approval processes. Meeting those needs requires a system that can support more decentralized, flexible control. If not addressed, organizations will lose control over a growing portion of their digital workforce.
The risks of poor non-employee governance
Where unmanaged identities create exposure
Non-employees are usually subject to less control. Ineffective or delayed revocation of access leaves the door open to unauthorized use, accidental exposure, or deliberate misuse.
These threats are not just hypothetical. In 2025, third-party access breaches jumped significantly, with 30% of all reported breaches resulting from vendor or contractor accounts. Several of the incidents traced back to misconfigured access or unused accounts that were never deprovisioned.
Real-world consequences
A recent healthcare incident was reported where a vendor-driven breach led to 437,000 patient records to be exposed, compromising care and triggering investigations, and put added emphasis on the regulation of industry non-employee users.
In the banking industry, a bank was one of 20 global customers hit by a vendor/provider data breach, resulting in over 130,000 employee records to be leaked. The records included executive and board members' personal data, demonstrating the speed with which third-party risk can turn into enterprise risk.
Third-party vendor-caused incidents and supply chain incidents are the one of the costliest, with an average cost of $4.91 million per incident, as IBM found in a recent study. Such attacks also take the longest to detect and contain at nearly 9 months.
Gaps in transparency and responsibility
Without defined processes for non-employee governance, orphaned accounts can remain open after a project is over. Access can extend far beyond the original intention. In some cases, there are multiple different identities for the same user within multiple different departments or contracts.
Lack of centralization for ownership also makes it difficult to hold an individual accountable. It is difficult to establish someone accountable for access approval, monitoring, or revocation when different business units share a single vendor.
These governance failures place organizations at additional risk. They also limit an organization’s ability to demonstrate compliance when requested audit or respond promptly when dealing with a breach.
What effective non-employee governance looks like
A third-party user governance model
The majority of companies recognize the risk but still only use manual systems or rely on systems not designed for non-employees. A complete approach requires both structural and procedural controls.
Good third-party identity governance is built on visibility, accountability, and automation, not by simply replicating employee IAM policies. It is about developing a unique governance model that is tuned for the fragmented and time-bound nature of external access.
Key elements of good non-employee governance
Organizations with well-governed non-employee identities have the following practices:
Centralized visibility
Unified view of all non-employee users, affiliations, and active access levels—regardless of the team that onboarded them.
Lifecycle control automation
Systems that can automatically terminate identities and access depending on contract length, project timelines, or sponsor approval.
Vendor-delegated administration
Business units or external managers are tasked with initiating requests for onboarding, but the final access decisions still go through the standardized processes.
Project- and expiration-based access
Users are granted access only when they are actively engaged or linked to a particular project, rather than given unrestricted roles.
Audit-ready governance
All decisions, from the initial request all the way to the access reviews, are documented and traceable, supporting internal and external audit requirements.
Establishing consistency across the organization
The goal is to build repeatable, scalable processes for non-employee identity management. When each department defines access in its own terms, inconsistencies can happen. Central governance gives the confidence that policies are applied consistently, without limiting operational flexibility.
Common pitfalls in non-employee governance
Patterns that create exposure
The majority of vendor and contractor incidents happen, not because of technical gaps, but rather as a result of governance lapses. Organizations have basic IAM practices established but consistently fall back on common patterns that yield unmanaged or under-monitored third-party access.
Some of the most common pitfalls include:
No assigned ownership
If no single person is accountable for third-party user access, unchecked approval of requests is possible and deprovisioning can be delayed or overlooked.
Shared or generic accounts
Vendor teams share credentials, which can make it more difficult to detect unauthorized access or identify “who did what”. This is not auditable.
"Just in case" access
Access is preemptively granted without an assigned task or termination date. These accounts exist perpetually, adding risk for no apparent reason.
No centralized visibility
Every department can onboard external users separately. With no system of record in place, the company cannot assure at any moment who has access to what systems.
Tracking access manually (through email, spreadsheets, etc.)
Requests, approvals, and changes are done ad hoc, causing failure, inconsistency, and lost audit trails.
These gaps and failures often become apparent only after a breach has occurred and an investigation takes place, but by then, it’s too late.
How idGenius transforms non-employee governance
The limits of traditional IAM solutions
IAM solutions for employees typically follow a consistent model: new hire events in HR trigger provisioning, role-based access is granted, and deactivation happens at termination. The model works for employees but breaks when applied to third-party users.
idGenius is designed specifically to manage the entire lifecycle of non-employee identities. It replaces fragmented onboarding and spreadsheet-based tracking with automated workflows that connect business needs to access within systems in a controlled, audited way.
By correlating access with contracts, projects, and vendor relationships, idGenius allows organizations to close governance gaps created by traditional IAM solutions.
Key idGenius features
Identity lifecycle and automation
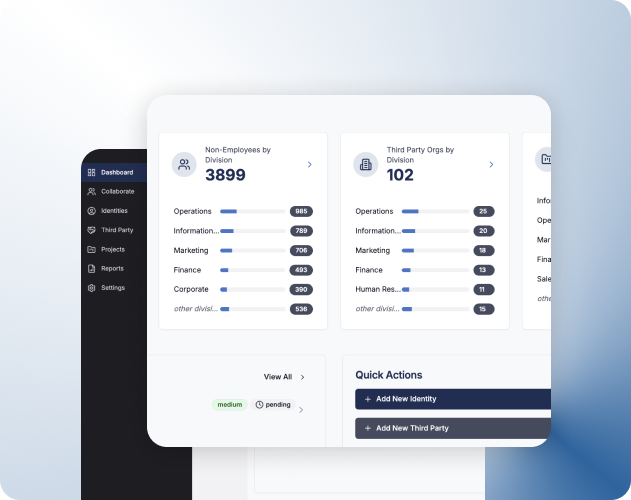
• Centralized onboarding forms tailored for vendor, contractor, and temporary roles
• Role- and project-oriented provisioning rules
• Self-expiring access upon project completion or contract end
• Real-time views into non-employee access across systems
• Support for multiple identity types, such as human and machine identities
• Out-of-the-box integrations with process automation tools
These capabilities provide end-to-end consistency in non-employee identity management, regardless of HR data and manual deprovisioning.
Secure vendor management and delegated administration
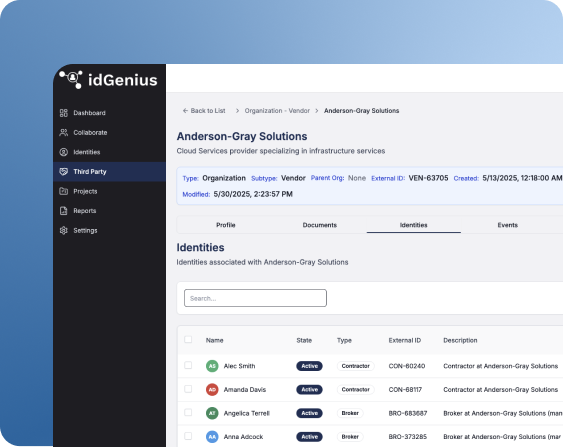
• Organize external users by organization or vendor, not as individuals
• Designate vendor managers to govern their own groups
• Allow vendor managers to initiate requests
• Track and review vendor-specific documentation, i.e., contracts or certifications
• Minimize IT involvement while maintaining accountability and auditability
Vendor-delegated administration helps ensure that external access correlates with business ownership without bypassing governance requirements.
Compliance and risk alignment
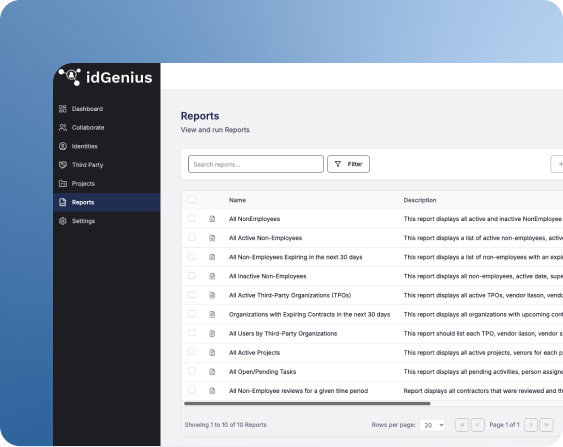
• Fully auditable trails for requests, approvals, and access changes
• Vendor, user, or project-level access reviews
• Documentation tracking for compliance (e.g., SOC reports, ISO certifications)
• Support for time-based and project-scoped access
• Configurable notifications for expiring access or pending approvals
These capabilities tackle vendor risk and compliance requirements while making audit readiness easier to maintain.
idGenius brings order to what is usually an ad hoc, fragmented process. It enables organizations to manage non-employee access with the same level of granularity they apply to internal users—without compromising flexibility.
Real-world use cases for idGenius
Healthcare: Temporary clinical staff
Numerous health systems and hospitals rely on resident physicians, traveling nurses, and contracted specialists. These non-employees may require access to electronic health record systems, internal portals, and protected communications.
With idGenius, hospitals can provision access tied to every clinical rotation or assignment, so users are offboarded when their engagement is finished. Vendor organizations can submit user rosters directly, and expiration policies ensure time-limited access is provided. This reduces dependence on IT teams while still providing visibility into compliance with HIPAA and other healthcare regulations.
Financial services: Broker and agent access
Financial services firms typically work with external agents, brokers, and consulting partners, and these third-parties may require access to customer data or CRM platforms.
idGenius offers company or individual onboarding, so business teams can approve access based on firm affiliation and project scope. The system also logs each approval and enforces expiration dates, restricting long-term exposure.
Technology and manufacturing: Project-based contractors
For technology, consulting, and manufacturing industries, external developers, engineers, and technicians are frequently employed to perform short-term work. These workers may need admin permissions to dev environments or production equipment.
idGenius provides fine-grained control of access by allowing it to be assigned based on project or contract, rather than based on static roles. Delegated approval ensures that only necessary access is granted, while automated deprovisioning helps reduce orphaned accounts.
Best practices for implementing non-employee governance
From awareness to action
Most organizations realize that they must improve how they manage third-party access but have no idea where to begin. Governance issues typically cross more than one department, system, and process. Addressing them requires collaboration within business teams, IT, and security.
Rather than performing this once as a one-time cleanup, organizations are better off treating non-employee governance as an ongoing, policy-driven function. The best practices listed below can serve as a starting point.
Recommended implementation steps
1. Inventory non-employee identities
Start by identifying all third-party users across departments and platforms. These are contractors, vendors, and service accounts that are not processed through the HR system.
2. Match access to business purpose
Associate each request for access with a contract, project, or internal sponsor. Never grant access without a defined scope and termination.
3. Standardize onboarding and approvals
Use centralized request forms and authorized workflows. Include authorized delegated input by business owners or vendor managers where appropriate.
4. Enable monitoring and periodic review
Maintain visibility on all active non-employee accounts. Have recurring reviews scheduled to confirm that access is still needed and well-scoped.
5. Automate offboarding and expiration
Apply time-based expiration policies and remind business stakeholders when access should expire. Automatically de-provision inactive accounts where possible.
Following these steps reduces exposure and offers a better basis for vendor risk and compliance programs.
Conclusion + strategic recommendations
The rise of third-party breaches in recent years has ensured one thing: non-employee governance can no longer be an afterthought. While contractors, vendors, and partners remain a core component of business procedures, organizations must have capabilities in place to manage their identities securely and reliably.
Reliance on traditional IAM tools or manual monitoring introduces unwarranted risk. Central visibility is absent, offboarding is irregular, and approvals are delayed, all resulting in operational and compliance loopholes. To address these, organizations need a governance model suited to the structure and requirements of non-employee users.
idGenius delivers a formal process of third-party identity governance—one based on secure vendor management, delegated access, and lifecycle control. Organizations that want to reduce third-party exposure, remain in regulatory compliance, and simplify identity management should consider their current non-employee access processes and whether purpose-built solutions should be used to improve them.
Contact our team at info@anomalix.com to learn more today.
Mohammed Elkhatib is Founder and CEO at Anomalix. Prior to founding Anomalix, Mohammed led global operations for Aveksa (acquired by RSA) where he was responsible for Sales, PreSales, Engineering and Professional Services. Mohammed is an Identity Security expert with over 25 years of IT and Business experience.



