Non-human vs. Machine Identities: What They Are and How to Manage Them
The way in which organizations view identity has changed. It's not merely about managing logins for employees and contractors anymore. More and more of the access activity that occurs is tied to entities that aren’t even human.
These non-human identities (NHIs)—bots, service accounts, and APIs—are now playing vital roles in cloud platforms, automation pipelines, and software environments. Though they may be created and destroyed within a matter of minutes, they can hold sensitive permissions or persist for weeks—much longer than they need to.
While this transformation introduces agility and scale, it also adds complexity. This blog examines how these two commonly grouped things (machine and non-human identities), though similar, have their own differences. By understanding the difference, and the risks and responsibilities involved in each, security teams can create better plans to manage access at scale.
What are non-human identities?
Not every identity belongs to a person
An identity typically refers to any entity that can be authenticated to gain access to data or systems. Although most teams focus on end users, employees, and partners, there are other things identities can be tied to, such as scripts, services, devices, and automated tools. These are all non-human identities.
Common types of non-human identities are:
• Service accounts used by applications to connect with databases.
• Bots talking to users or running scheduled jobs.
• APIs used for transferring or receiving data from one system to another.
• IoT devices like printers, cameras, or medical equipment.
• Scripts and automated activities that run in CI/CD pipelines.
They're growing quickly—and more than ever
The number of non-human identities is increasing at a very rapid rate. Most organizations are now handling more non-human identities than human ones. Experts estimate the ratio to be about 82:1 and rising. AI systems are increasing that growth by introducing new service identities for agents, models, and cloud resources.
However, this convenience comes at a price. Non-human identities can authenticate and do the tasks that human users do, yet they’re often overlooked during things like audits or access reviews.

What are machine identities?
A narrower category within non-human identities
Machine identities are a subgroup of non-human identities. They're used by machines—like servers, containers, and software processes—to authenticate and securely communicate with each other. They verify one service to another and are extensively used within backend infrastructure.
Some examples include:
• TLS/SSL certificates securing web traffic
• SSH keys allowing system access for automated tools
• Kubernetes pod or workload identities
• Cloud service accounts used by containers and applications
• API tokens stored in automated workflows
They're everywhere, yet they’re often left unchecked
Over time, machine identities have increased in number. Every new deployment pipeline, microservice, or container can give rise to dozens of machine identities. These identities can be made in a hurry, utilized for a short period of time, and at the end, they’re often forgotten just as fast, bringing a fair amount of risk.
79% of security teams expect their number of machine identities to increase within the coming year. Machine identity management is emerging as an integral part of identity security. It's not just about counting the number of identities. It's knowing what they can do, who they're owned by, and how long they should exist.
Non-human vs. machine identities: What’s the difference?
The labels are often used synonymously, but they're not the same
All machine identities are non-human, but not all non-human identities are machines. It's a simple distinction that has practical implications for the way access is governed and audited.
Non-human identities are identities that aren’t human but that also need access to a system. That includes machine identities, but also scripts, bots, APIs, and physical devices as well. Machine identities are a subcategory, employed primarily by software systems for authentication with one another.
Key differences between non-human and machine identities
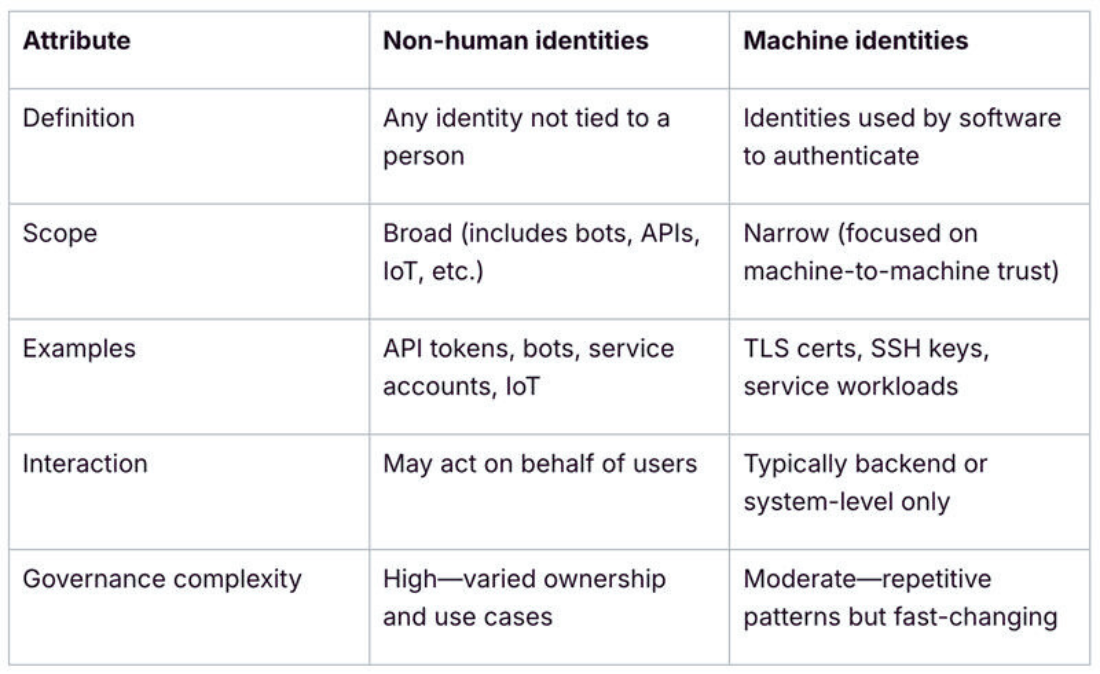
Why it matters
Non-human identities often have a range of use cases, inconsistent behavior, and unclear ownership. That makes them harder to monitor and control.
Machine identities, while more predictable in their action, need to be handled with equal care throughout their lifecycle as well. Their high rate of growth, short lifespan, and elevated access make them just as important to control. Having a clear understanding of the difference helps teams put the proper controls, policies, and tools in place. It also helps ensure that the mistake of treating all non-human identities the same (regardless of their purpose or risk) isn’t made.
Common risks associated with non-human Identities
More access, fewer eyes on them
Non-human identities often operate with minimal oversight. They're not on onboarding checklists. They don't submit request tickets for access. They're often provisioned in code, rather than by explicit request. That makes them vulnerable to being forgotten and misused.
If poorly managed, these identities create avenues for a wide range of security issues:
• Orphaned accounts remain after projects are finished, with no specified owner.
• Secrets stored in scripts or containers are hardcoded, making them retrievable and reusable.
• Static credentials are cached for months and years without rotation.
• Service accounts are over-provisioned and have more access than they need.
• Teams do not have visibility to identify idle or high-risk identities.
The numbers are telling
Current statistics reveal just how serious the problem is:
• 50% of companies experienced a security incident with a machine identity during the past year. Of these companies, 51% faced delays in application launches, affecting production timelines; 44% reported outages, impacting customer experiences and brand reputation; 43% reported unauthorized access to sensitive systems.
• 72% of companies had certificate-related outages due to mismanagement, occurring on a weekly basis at times.
• 77% of security leaders believe every unmanaged machine identity is a threat.
Governing the lifecycle of non-human and machine identities
Why lifecycle management matters
Every identity has a beginning, a purpose, and an expiration. Service accounts, certificates, bots, and tokens are no different. If non-human identities aren't managed through their full lifecycle, they linger—with permissions they no longer have. This is where most companies get stuck.
Machine identities are often created automatically/in a rush. Without an official process for managing them, they can accumulate, expire without notice, or fall into the wrong hands.
Lifecycle phases
Good governance starts by learning what the lifecycle actually is:
• Provisioning: An identity is created, typically as part of a deployment pipeline, cloud instance, or integration setup. Who creates it? What systems will it authenticate to? What permissions will it need?
• Use and rotation: The identity gets utilized—connecting to APIs, authenticating workloads, or accessing secrets. Are credentials short-lived or long-lived? Is there a key, token, or certificate rotation policy?
• Monitoring: Is the identity in use? Are there signs of over-use, inactivity, or odd behavior?
• Deprovisioning: If the identity is not needed anymore, is it removed? Is the access revoked in full, or just left dormant?
Governance practices that pay off
Lifecycle activities are only as effective as the policies and tools that work alongside them. The following are practices organizations should employ to improve their identity security posture:
• Give ownership to every identity—whether human or non-human. Someone has to own it in order to monitor, update, and retire it.
• Use least privilege by design. Identities should only be given access to what they need.
• Automatically rotate credentials to eliminate static tokens and secrets.
• Use expiry for service accounts, API keys, and certificates. Treat them like perishable goods.
• Use discovery tools to continuously map and monitor non-human identities throughout cloud environments.
Structure reduces risk
Without structure, non-human identities accumulate. With it, you get visibility, reduced exposure, and a guarantee that credentials rotate when they are required to.
Build an identity-first strategy for all users
Machine and other nonhuman identities now make up the majority of digital identities in most organizations. They power automation, cloud infrastructure, and business operations, whilst also introducing new risks if not effectively governed.
Having the ability to determine if a non-human identity is machine or non-machine enables security teams to deliver focused governance, apply the right lifecycle controls, and reduce exposure based on access. Service accounts, tokens, certificates, and automation scripts all require the same level of scrutiny traditionally applied to human users.
The risks are clear. From API key exposure to certificate outages, real-world incidents have shown us how non-human identities can cause disruption or be exploited as entry points by attackers. They cannot be neglected.
As identity security evolves, successful organizations are considering it more broadly. They're building systems that treat every identity—human or not—as a potential attack surface. That means extending ownership, expiry, and least privilege to all. Contact info@anomalix.com today to learn how we can help you build a stronger, more dependable access model.



