Non-Employee Identity Governance: The Missing Layer in Your 2026 Cybersecurity Strategy
Non-employee Identity Governance is the missing layer in most cybersecurity strategies because it governs the identities that create the largest blind spots: contractors, vendors, partners, consultants, and machine accounts that rarely pass through HR and traditional IAM workflows. From Anomalix’s point of view, this is no longer a “nice-to-have” capability but a strategic control layer that determines whether your extended workforce becomes an asset—or a persistent source of cyber risk.
Introduction: The Identity Layer You Forgot
Most organizations have invested heavily in employee identity and access management. HR feeds the IAM system, roles are modeled, and joiner–mover–leaver processes are defined—at least for full-time staff. But outside that well-governed core sits an ecosystem of non-employees: contractors, service providers, integrators, temporary staff, offshore teams, and an expanding universe of APIs, bots, and service accounts.
These identities are essential to how modern business runs, yet they are often tracked in spreadsheets, emails, slack messages, and manual tickets instead of a unified identity system. That gap is where risk accumulates - orphaned accounts that never get shut off, over-privileged vendor admins, long-forgotten integration keys, and inconsistent offboarding that leaves doors open for months or years.
From an Anomalix perspective, non-employee identity governance is the missing identity layer—sitting between your core IAM/IGA stack and your extended ecosystem—designed specifically to govern external and non-human identities with precision, automation, and zero-trust rigor.
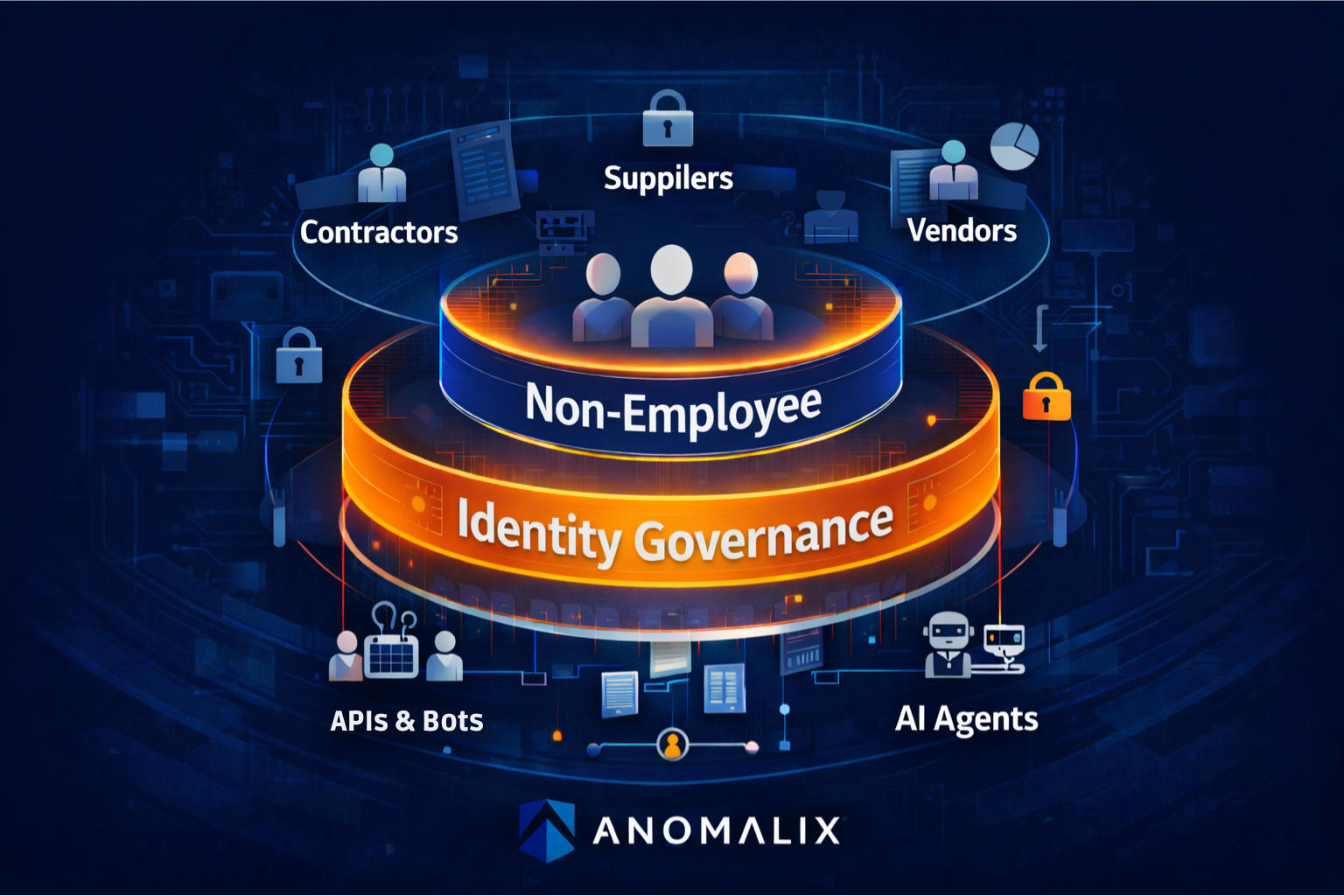
What Is Non-Employee Identity Governance?
Non-employee Identity Governance is the discipline and technology used to manage identities and access for anyone (or anything) that is not a full-time employee in your HR system. It encompasses human and non-human identities such as:
Contractors and consultants
Vendors, suppliers, and managed service providers
Partners and affiliates
Temporary or seasonal workers
Students, interns and board members
APIs, service accounts, bots, and AI agents that integrate into your environment
Unlike traditional IGA, which is usually anchored to HR as the system of record, non-employee identity governance must pull context from contracts, vendor agreements, project scopes, and external directories. It needs to understand not just “who” someone is, but “for which organization,” “on which project,” and “for how long,” so that access is always bound to real-world engagement details.
Why Non-Employee IAM Is the Missing Layer
The modern enterprise runs on an extended digital supply chain, and many of the riskiest identities now sit outside the firewall—both literally and logically. The problem is that most cybersecurity strategies were never updated to treat those identities as first-class citizens in the identity fabric.
When non-employee IAM is missing or immature, several chronic issues emerge:
Fragmented sources of truth
Non-employee data lives in procurement tools, contract systems, email threads, and local spreadsheets, rather than in one authoritative identity store.
Manual, inconsistent onboarding and offboarding
Different business units “do their own thing,” sending ad hoc tickets to IT or granting direct access in SaaS tools, which leads to delays, errors, and inconsistent privilege patterns.
Over-provisioned and orphaned accounts
Contractors get broad access “just to get them started,” and when engagements end, nobody is sure which accounts to revoke or which entitlements they still have.
This is precisely the layer Anomalix focuses on: governing the join–change–leave lifecycle for non-employees with the same rigor as employees, but using models and workflows that reflect how third parties actually engage with your organization.
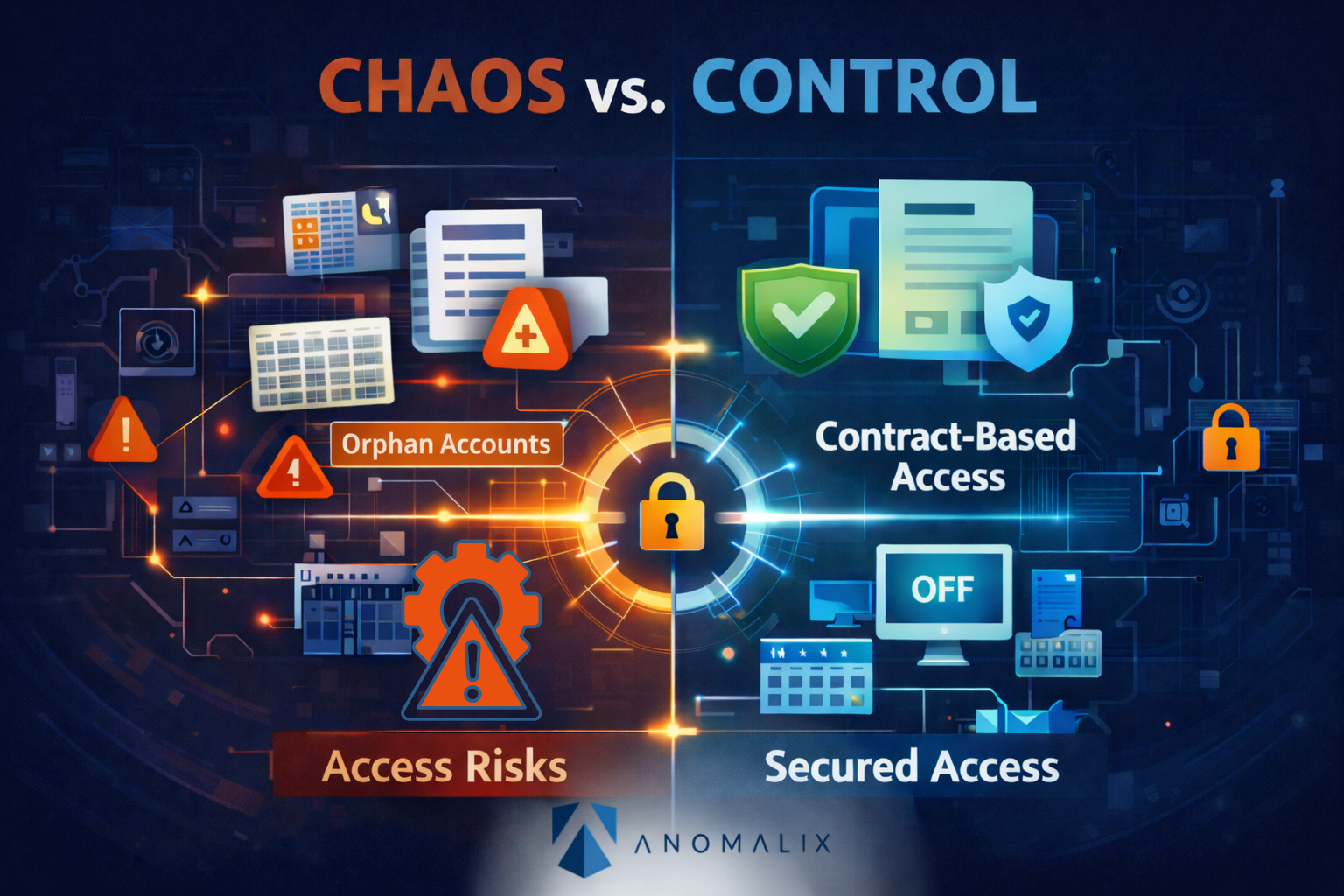
The Hidden Risks of Ignoring Non-Employee Identities
From a risk standpoint, non-employee identities behave differently—and often more dangerously—than internal users. They change employers, move between projects, and sometimes work across multiple client environments at the same time.
Some of the most critical risks include:
Orphaned and dormant accounts
Vendor staff leave their company, contracts end, or projects pause, but credentials remain active in your systems, creating a ready-made attack vector.
Over-privileged access and scope creep
As non-employees move between projects or teams, access is added but rarely removed, expanding exposure far beyond the original engagement scope.
Shadow access and informal processes
Business users bypass formal channels (“just give them a VPN account so they can start today”), leading to unmanaged entitlements and untracked access paths.
Third-Party Risk for organizations only
Most organizations perform a one-time risk assessment for their third-party relationships. The risk rating remains static at the organizational tier and is never inherited by identities from those organizations.
Third-party breach amplification
When a vendor’s environment is compromised, attackers can use non-employee accounts as a bridge into your systems if those identities are poorly governed.
Without a dedicated non-employee IAM layer, these risks remain hidden in the cracks between vendor management, IAM, and security operations—until an audit or incident brings them painfully to the surface.
Why Traditional IAM/IGA and Vendor Management Aren’t Enough
Many organizations assume they can handle non-employees by stretching existing IAM/IGA or vendor management tools, but this is where architectural limitations show.
Traditional IAM/IGA challenges:
HR-centric identity models
IAM systems usually rely on HR as the authoritative source. Non-employees rarely appear in HR, so they are modeled as edge cases, generic accounts, or duplicates.
Limited contract and organization context
Standard IAM is not built to understand that one identity belongs to a third-party company, maps to multiple projects, and must be governed differently than internal staff.
Missing Document Management and e-Signature
Standard IAM was never built to capture, store or sign documents, contracts or provide consent management capabilities.
Missing Project context
IAM systems have no context of projects that often require different requirements, credentials and onboarding workflows that often involve multiple third-party organizations.
Vendor management limitations:
Focus on contracts, not identities
Vendor management tools track legal and commercial relationships but typically do not control specific user accounts, privileges, or system access.
Weak lifecycle linkage
Contracts can expire while accounts stay active, because there is no automated binding between vendor lifecycle and identity lifecycle.
From Anomalix’s perspective, non-employee IAM must be purpose-built—sitting at the intersection of identity governance, third-party risk, and vendor lifecycle automation, rather than bolted on to employee-centric or contract-centric systems.
Anomalix POV: Identity-First, Non-Employee-First
Anomalix takes an identity-first view of cybersecurity: identity is the new perimeter, and non-employee identities are often the weakest links when unmanaged. The answer is not more manual review; it is a deliberate architecture that treats non-employees and third parties as a distinct but fully governed population.
Key principles in the Anomalix approach:
Single source of truth for ALL third-party organizations and non-employees
Centralize all third-party organizations and all external identities—people and machines—in a unified directory that includes contracts, parent organizations, sponsors, project scopes, dynamic risk scores and expiration dates.
Contract- and project-driven lifecycle
Join, change, renewal, and leave events are tied to contracts and projects; when a contract ends, access is revoked automatically, not when someone remembers a ticket.
Zero-trust access by design
Non-employees receive least-privilege, time-bound access, with continuous validation and re-evaluation when context or risk changes.
Manage Third-Party Risk for organizations and identities
Identities inherit baseline risk ratings from the parent organization and is used in calculating individual risk scores based on geography, background checks, identity verification and project access.
Non-employee and Third-Party Identity governance is not a sidecar to IAM; it is a dedicated governance fabric for the extended workforce, designed to plug into your existing IAM, PAM, ITDR, and overall cybersecurity stack.
How Non-Employee IAM Works in Practice
A mature non-employee IAM program follows a lifecycle that parallels—and often improves on—the employee lifecycle: onboarding, managing changes, and offboarding. The difference lies in the inputs and automation patterns.
High-fidelity non-employee onboarding
Onboarding starts with structured, source-driven intake rather than loosely defined access requests.
Business sponsors or vendor owners complete guided forms that capture identity type, organization, contract dates, project scope, and required systems.
Approval workflows ensure the right stakeholders sign off before any account is created, capturing accountability from day one.
Once approved, access is provisioned automatically according to policies, rather than manually recreated each time.
This high-fidelity onboarding eliminates ambiguity and sets a strong foundation for every future access decision.
Managing changes with closed-loop automation
Non-employees often shift roles, move between projects, or change reporting lines more frequently than employees. A non-employee IAM layer ensures these changes are governed, not improvised.
Any change in contract, project, or role triggers a policy-driven evaluation of access, adding or removing entitlements as needed.
Business owners remain in the loop but operate through simplified, guided workflows rather than ad hoc requests.
This closed-loop automation prevents scope creep and reduces the chance that yesterday’s “temporary” access becomes tomorrow’s high-risk standing privilege.
Secure, automated offboarding
Offboarding is where many organizations carry the most risk, and where Anomalix places heavy emphasis.
Identities are created with natural expiration dates tied to contract terms, ensuring accounts do not live beyond the engagement unless explicitly renewed.
When a contract ends, the system systematically revokes access across all systems—directories, VPN, SaaS apps, data stores, and collaboration spaces.
Every action is logged, providing audit-ready evidence for regulators, customers, and internal stakeholders.
This turns offboarding from a memory-based task into a deterministic, governed identity event.

Where idGenius Fits: The Purpose-Built Non-Employee IAM Layer
idGenius from Anomalix is the platform built specifically to operationalize this non-employee IAM layer. It is not an IGA afterthought; it is a purpose-built system for managing third-party and machine identities with agility, contextual intelligence, and automation.
Core capabilities include:
Unified visibility into third-party organizations and identities
idGenius maintains an inventory of non-employees and the organizations they belong to, including access timelines, engagement details, and risk profiles.
Project- and contract-based provisioning
Access is granted and time-bound at the project or engagement level, reducing over-provisioning and making renewals explicit rather than implicit.
Document and consent management
Built-in workflows for storing contracts, attestations, and required documents ensure that compliance artefacts stay attached to the identities they govern.
AI-driven anomaly detection and remediation
The platform analyzes behavior and access patterns to flag anomalies, trigger reviews, or even drive near-real-time remediation.
idGenius is designed as a light, focused SaaS layer that pairs with existing IAM/IGA stacks, making it easier to modernize non-employee IAM without replacing everything you already have.
Non-Employee IAM, Zero Trust, and Compliance
Non-employee IAM is not just an operational win; it is deeply tied to zero-trust security and regulatory compliance.
Zero-trust architectures assume no implicit trust based on network location or employment status, which means non-employees and machine identities must be governed with the same rigor as internal users.
Standards and frameworks such as ISO 27001, SOC 2, GDPR, and industry regulations increasingly expect organizations to control third-party access, prove timely deprovisioning, and demonstrate least-privilege enforcement.
By aligning non-employee lifecycle controls with these frameworks—through contract-bound access, automated deprovisioning, and detailed audit trails—organizations reduce audit fatigue, shorten assessment cycles, and strengthen overall posture.
Conclusion: Make Non-Employee IAM a First-Class Citizen
Non-employee IAM is the missing layer that ties your extended workforce, digital supply chain, and machine ecosystem into a coherent security strategy. As more identities belong to people and systems outside your HR domain, ignoring this layer is effectively choosing to leave parts of your environment in the dark.
Anomalix’s point of view is unequivocal: govern external identities with the same rigor—and often greater contextual intelligence—as internal staff, using identity-first modeling, closed-loop automation, and zero-trust controls. With a purpose-built platform like idGenius, enterprises can finally bring non-employee IAM into the center of their cybersecurity strategy, reducing risk, strengthening compliance, and enabling the extended workforce to move at the speed the business demands.
Contact us at info@anomalix.com to learn how our idGenius platform can help you govern your extended workforce with confidence, security, and ease.
Mohammed Elkhatib is Founder and CEO at Anomalix. Prior to founding Anomalix, Mohammed led global operations for Aveksa (acquired by RSA) where he was responsible for Sales, PreSales, Engineering and Professional Services. Mohammed is an Identity Security expert with over 25 years of IT and Business experience.



