Managing Non-Employee Risk: A Modern Approach to Third-Party Identity Governance
In today’s hyper-connected business world, the boundaries of the traditional workforce have expanded far beyond full-time employees. Organizations now rely on a vast ecosystem of consultants, contractors, contingent workers, vendors, partners, and even non-human identities such as APIs, bots, and service accounts.
While these external entities drive efficiency and innovation, they also introduce new layers of complexity and risk. Mismanaged access can expose sensitive systems, violate compliance mandates, and erode trust.
As organizations evolve, so must their approach to managing non-employee identities — not as an afterthought, but as a strategic pillar of governance. Modern enterprises increasingly recognize that identity is the new security perimeter, and the ability to manage identities effectively — whether internal or external — determines an organization’s resilience and agility in a digital-first world.

1. What Is Non-Employee Risk Management?
In simple terms, Non-Employee Risk Management is the practice of managing, monitoring, and securing access for anyone or anything that interacts with your organization without being on your direct payroll — including contractors, consultants, and APIs. Without proper controls, such identities can linger indefinitely, leaving organizations vulnerable to breaches and compliance issues. Modern governance brings these identities under the same rigor as internal users, ensuring visibility, lifecycle control, and accountability. This concept is increasingly critical as remote work, outsourcing, and automation reshape business operations, turning identity governance into a strategic enabler of trust.
The challenge is that these identities are frequently ephemeral, project-based, or highly dynamic, making traditional employee-focused identity governance approaches inadequate. Key issues include:
· Untracked Access: Third-party identities may retain access long after a project ends, creating unauthorized exposure.
· Fragmented Oversight: Non-employee identities often exist across multiple systems, cloud environments, and SaaS platforms, making centralized management difficult.
· High-Risk Credentials: Service accounts, API keys, and automated scripts often carry broad privileges and can be exploited if left unmanaged.
· Manual Processes: Onboarding, offboarding, and access changes are often performed manually, increasing the likelihood of errors.
Without a specialized governance platform, organizations face blind spots that can result in operational inefficiencies, compliance issues, and security incidents.
2. The Four Stages of Risk Management — Applied to Identity Governance
The ‘four stages of risk management’ — Identification, Assessment, Mitigation, and Monitoring. Applied to identity governance, these stages ensure every non-employee identity is tracked, assessed for risk, and continuously monitored. Anomalix embeds automation and AI to ensure no non-employee identity — human or machine — goes unmanaged or unmonitored. Each stage reinforces the other, creating a closed-loop system that not only detects risk but adapts over time, learning from behavioral data and operational patterns to improve governance efficiency.
3. Who Is Responsible for Third-Party Risk?
Responsibility is shared across IT, security, business owners, and compliance teams. Each stakeholder plays a part — business units define access needs, IT enforces policies, and compliance ensures adherence. Modern governance solutions unite these roles through a single pane of glass, ensuring transparency and accountability. This shared responsibility model empowers organizations to move faster while maintaining security alignment, fostering a culture where governance is seen not as bureaucracy but as a foundation for collaboration and trust.
4. Human and Machine Identities — A Unified Approach
Modern enterprises must manage both human and machine identities equally. APIs, bots, and service accounts can hold powerful credentials that often go unchecked. Anomalix treats all identities as first-class citizens, applying lifecycle policies, risk scoring, and automated deprovisioning to eliminate blind spots and ensure total governance. This unified governance approach breaks down silos between departments and systems, delivering a cohesive view of all digital access relationships — an essential capability in hybrid and multi-cloud environments.
5. AI-Driven Risk Detection and Adaptive Analytics
Traditional governance tools rely on static rules, but AI introduces adaptive intelligence. By analyzing behavior, AI detects anomalies such as off-hour logins or suspicious data access. This proactive capability turns governance into a responsive, living defense system — a hallmark of the Anomalix approach. Over time, these intelligent systems learn from patterns and refine their accuracy, enabling proactive interventions before risks escalate, and helping organizations predict potential vulnerabilities rather than simply react to them.
6. Compliance and ISO Alignment
ISO 27001 and ISO 31000 require organizations to control supplier access. Modern platforms aligns with these frameworks by embedding compliance into everyday operations. Point-in-time visibility and audit-ready reporting simplify certification and reduce manual workload. Moreover, by aligning governance processes with ISO standards, organizations not only meet regulatory expectations but also establish a framework of continuous improvement — enhancing resilience and readiness for future compliance changes.
7. Delegated Onboarding and Time-Bound Access
Fast-moving business environments demand agility. Delegated onboarding allows departments to safely grant access to contractors or partners within secure boundaries. Policies ensure access automatically expires when a project concludes, minimizing risk and reducing IT dependency — empowering collaboration without compromise. This approach emphasizes simplicity and scalability, enabling global enterprises to onboard hundreds of external users quickly while maintaining strict adherence to corporate policies and security baselines.
Modern platforms provide delegated onboarding workflows that allow business teams to provision access safely while enforcing policy and compliance requirements automatically.
· Delegation: Business teams can onboard contractors or partners without granting full administrative privileges.
· Policy enforcement: Access is provisioned based on predefined policies, ensuring least-privilege principles are maintained.
· Efficiency: IT teams are freed from repetitive onboarding tasks, allowing them to focus on higher-value activities.
8. Lifecycle Management and Continuous Oversight
Every non-employee identity follows a lifecycle — from onboarding to modification to offboarding. Automation ensures consistency and eliminates human error. With AI-driven monitoring, organizations maintain constant visibility, ensuring that access evolves with role changes and is revoked promptly when no longer needed. This closed-loop automation also supports adaptive governance, dynamically adjusting access privileges based on risk level, compliance requirements, or business context.
Non-employee identities often pose challenges during audits, compliance assessments, and internal reviews. A robust governance platform provides point-in-time visibility into access, enabling organizations to demonstrate:
· Who had access to specific resources at any given time
· How access evolved over the lifecycle of the identity
· When automated offboarding and credential rotation events occurred
This visibility simplifies audits, reduces the manual effort required to gather evidence, and ensures compliance with internal policies, regulatory mandates, and industry standards. Historical reporting is particularly valuable for forensics, enabling teams to investigate incidents and identify risk trends over time.
9. Integration, Flexibility, and Real-World Application
Effective governance doesn’t operate in a vacuum. Anomalix’s integration-first design connects seamlessly with existing IGA, PAM, HR, and cloud systems. This architecture provides a unified source of truth. Real-world applications — from financial services to healthcare — prove that automation, visibility, and intelligence work best when integrated holistically. By integrating these capabilities, organizations can modernize without disruption, achieving quick wins while laying the foundation for long-term digital transformation.
10. Operational and Strategic Benefits
Implementing dedicated non-employee governance delivers measurable advantages:
· Reduced IT burden: Automated onboarding, modification, and offboarding reduce manual work.
· Lower security risk: Continuous monitoring, AI-driven detection, and automated remediation help prevent unauthorized access.
· Audit Readiness: Point-in-time visibility, audit trails, and automated reporting simplify compliance with GDPR, HIPAA, SOX, and other regulations.
· Business agility: Project-scoped access, delegated workflows, and flexible provisioning support faster engagement with vendors and contractors.
· Improved collaboration: Securely provisioned identities enable seamless collaboration with third parties without compromising security or compliance.
Beyond operational efficiency, these benefits build long-term strategic value, empowering organizations to scale confidently and respond rapidly to market dynamics.
Key Capabilities of Modern Non-Employee Governance Platforms
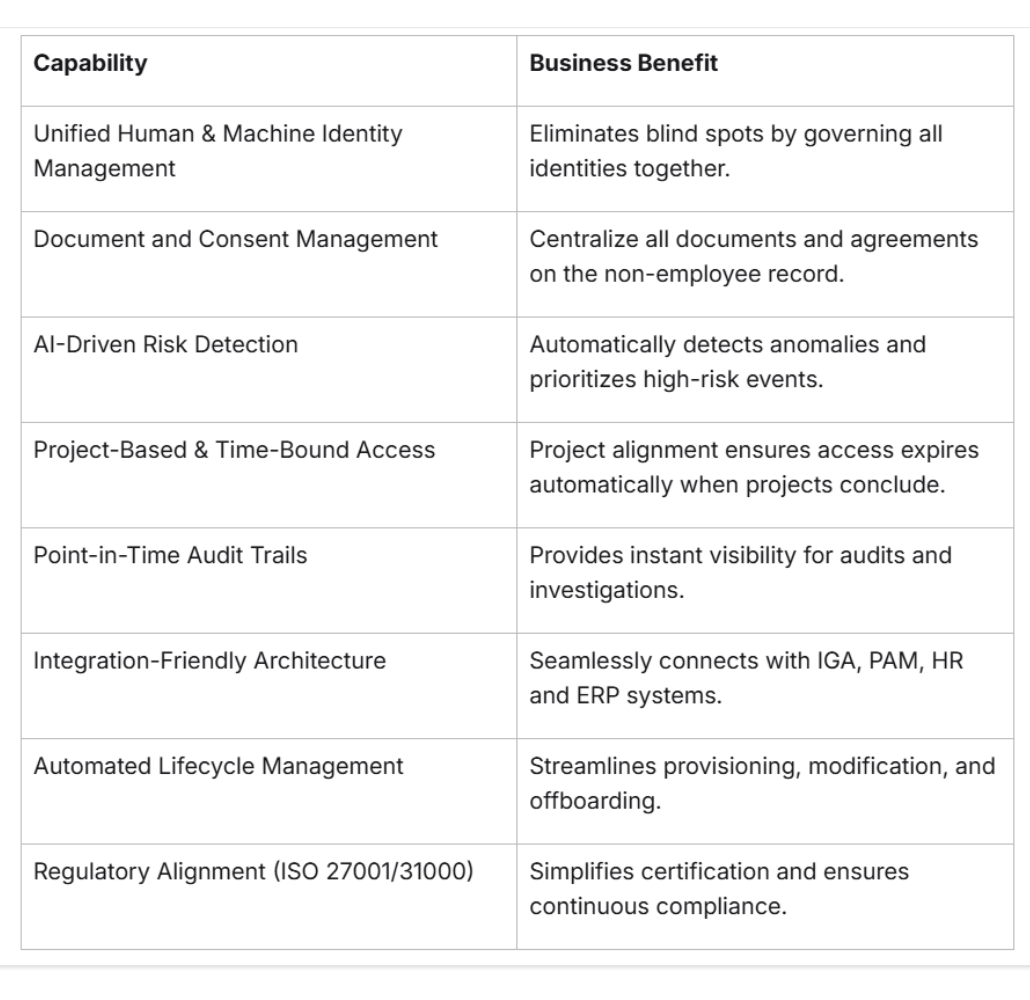
Anomalix: Redefining the Future of Non-Employee Risk Management
At the heart of modern identity governance lies a single truth — security must move as fast as business. Anomalix was built around this principle. As organizations extend their ecosystems to include contractors, vendors, partners, and intelligent automation, Anomalix enables them to maintain complete visibility and control without slowing innovation. The company’s purpose-built approach to non-employee governance transforms what was once a complex, manual process into a seamless, intelligent workflow that adapts to every stage of identity lifecycle management.
Unlike traditional IGA platforms that were retrofitted to handle external users, Anomalix designed its solutions from the ground up for today’s interconnected enterprise. Its architecture unifies human and machine identity governance, ensuring that every API, bot, and service account follows the same rigorous standards as human contractors. Through AI-driven analytics, Anomalix continuously learns from user behavior and environmental context — detecting anomalies in real time and automatically remediating risks before they escalate.
A defining strength of the Anomalix model is delegated autonomy — empowering business units to onboard and manage third parties safely while IT retains oversight. This democratizes governance across the enterprise, reducing operational friction and enabling faster collaboration. Combined with time-bound provisioning and automated offboarding, the platform eliminates the persistent risk of dormant or overprivileged accounts — a challenge that has plagued organizations for years.
Compliance is another pillar where Anomalix excels. By embedding ISO 27001, ISO 31000, SOC 2, and GDPR requirements directly into its workflow engine, the platform ensures that every identity event is traceable, auditable, and policy-aligned. Auditors gain instant, point-in-time visibility into access records, while security teams can generate evidence reports in minutes instead of days. This integration of governance and compliance transforms what was once a reactive effort into a proactive assurance mechanism.
Ultimately, Anomalix stands out not just as a technology provider but as a strategic enabler of secure digital transformation. In an era defined by borderless collaboration and machine-scale automation, the company’s vision is clear: to make identity governance simple, adaptive, and intelligent for every kind of user — human or non-human. By fusing automation with human-centered design, Anomalix empowers enterprises to govern confidently, operate efficiently, and innovate fearlessly in the age of distributed identity.

Conclusion — The Anomalix Perspective
Non-employee identities are now a defining feature of modern digital ecosystems. They power innovation but also expand the attack surface. Anomalix believes governance should not hinder collaboration — it should enable it. Through automation, AI, and unified visibility, organizations can eliminate blind spots and manage external identities confidently. This approach transforms compliance from a burden into a strategic advantage, empowering businesses to operate faster, safer, and smarter. As identity continues to evolve as the cornerstone of cybersecurity, organizations that prioritize intelligent, automated governance will not only strengthen their security posture but also achieve operational excellence in a landscape where agility and compliance must coexist.
To explore how Anomalix can help your organization strengthen non-employee risk management — with unified visibility, automated lifecycle governance, and AI-driven security intelligence — contact our team at info@anomalix.com and discover how to turn third-party identity risk into a strategic advantage.
Mohammed Elkhatib is Founder and CEO at Anomalix. Prior to founding Anomalix, Mohammed led global operations for Aveksa (acquired by RSA) where he was responsible for Sales, PreSales, Engineering and Professional Services. Mohammed is an Identity Security expert with over 25 years of IT and Business experience.



