


Identity and access management (IAM) protects critical applications and other resources by verifying that the people seeking access to them, really are whom they claim to be (identity management) and that they’re authorized to use specific resources (access management). For the modern organization, applications are in the cloud and on-premises, and users are as eager to access them from mobile devices and desktops, from anywhere, anytime.
Successful identity and access management demands more than user accounts and passwords. It requires analytics-driven insights into identities, a keen awareness of ever-changing cyber threats, and business context to identify risks and protect assets accordingly. Within IAM, some components and capabilities are more applicable to the workforce, as opposed to consumers.


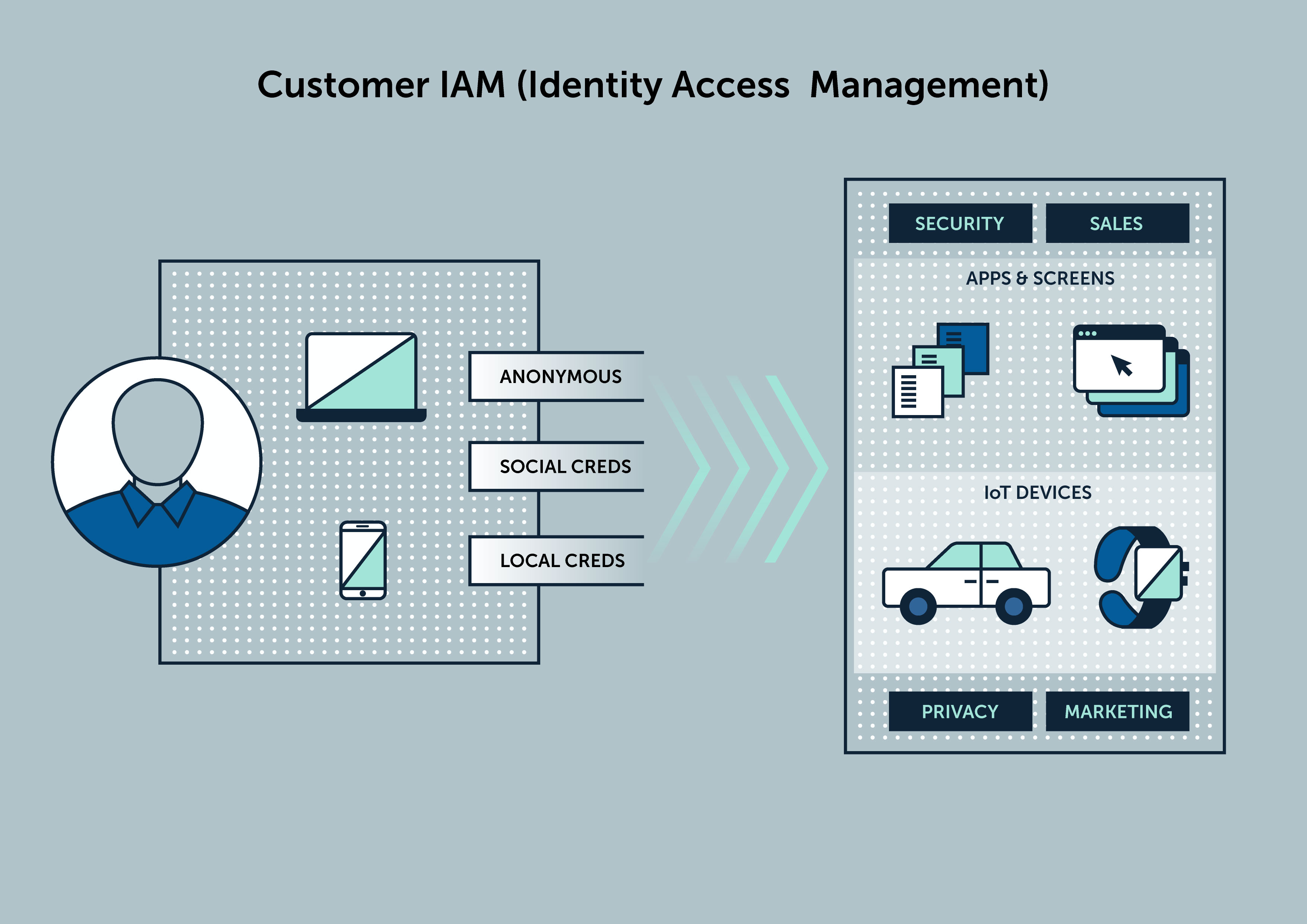
Establish an omnichannel presence for customers and consumers. Identify customers and enable registration and social credentials. Establish a holistic view and an authoritative source for customer records. Enable marketing and downstream applications and services with rich data for optimal personalization. Respect customer and consumer privacy settings and comply with regulatory mandates such as GDPR. Anomalix offers Customer AIM (CAIM) solutions on a purpose-built platform for the modern organization to increase sales.
Anomalix clients are able to:
Contact us to get started with your CIAM solution today.

Let us handle it! Anomalix IDaaS customers are up and running in days and are reducing the cost of managing access and compliance reporting by more than 50%
Anomalix’s Cloud-based Identity-as-a-Service Deliverables Include:

Privileged Access Management (PAM) is the process of granting, monitoring and protecting accounts with elevated privileges such as admin/root accounts. These privileged accounts are indispensable to run the business but the lack of privileged access management can lead to security breaches and compliance issues.
Anomalix helps organizations to mitigate and avoid business losses and financial penalties. In many organizations, developers, DBAs and other system administrators are given full super-user rights with little oversight. A lack of proper access governance for privileged accounts leads to an accumulation of excess privileges, orphaned accounts, ownership conflicts and other governance issues.
Organizations need to go beyond Password Vaulting methods and static policies to restrict and monitor privileged access. Eliminate the sharing of privileged accounts in order to improve auditability and personal accountability.

Anomalix Identity Analytics enable organizations to enforce a risk-based approach for Identity and Access Management in order to govern identities, control access, and manage privileged accounts. This approach to access analytics includes:

Data access governance helps organizations identify where business and compliance sensitive data resides, who owns it, who has access to it, and how users interact with it in accordance with GDPR, PCI, HIPAA and SOC2.
- Find data in documents, files, folders. storage devices and cloud applications.
- Gain visibility and ownership of user entitlements for cloud and on-premises environments: AWS, Azure, GCP, Box, OpenDrive, O365, Windows, Linux and Unix Servers, File Shares and Microsoft SharePoint.
- Automate the data access certification process for the lines-of-business.
- Remediate inappropriate access and put in place a consistent methodology for Active Directory group-based access to file shares and SharePoint.
- Enable a closed-loop validation process for change to data access permissions.
- Determine whether access policy and control objectives are being met.
- Manage data access risk and provide auditable evidence of compliance.

As organizations implement a Cloud First initiative to migrate on-premise data center functionality to cloud services, they can change the view of their data. Though they gain cost savings, they lose security and insight into their applications and infrastructure. Security must begin with visibility. Most organizations struggle to create a holistic view of user access permissions, resource inventories such as servers and databases, API traffic, and user activity within their public cloud infrastructure. Other common issues customers face in the cloud include:
+ Managing the outbound traffic
+ Limiting your exposure
+ Limiting SSH connections
+ Root/organization owner accounts
While cloud providers offer identity and access control tools, most organizations lack the corresponding policies that determine the minimum set of privileges to corresponding job responsibilities. Furthermore, security groups are not typically built with the least privilege model in mind, as the access required is often wide-ranging. Finally, turning on security logging and monitoring is imperative as it provides visibility to unauthorized access attempts, access/permission usage, API call information, and configuration deployment events.

Traditionally, Identity and Access Management (IAM) was concerned with the management of people, but now it is beginning to encompass hundreds of thousands of "Internet of Things" (IoT) devices. These IoT devices can connect to a network and communicate with the backend infrastructure (server, mobile device, etc.) to provide periodic updates and receive downloads.
The growth of IoT devices has been exponential, and as they become more and more pervasive in everyday life, there is a need to manage, support, and secure the IoT devices. The industry of identity management for IoT is still in its infancy, and now is the perfect time to determine how IoT devices can be integrated into existing IAM processes and security infrastructure.

Establish visibility, administration and control for every Identity. User Provisioning of access based on business controls and lifecycle events (Joiners, Movers and Leavers) is a key underpinning for Identity Management.
Automated user provisioning drives efficiency and enables a frictionless end-user experience. This has become a difficult task as the number of data elements for each Identity is increasing exponentially. It is more important than ever for organizations to have clear and actionable insight into Identity management in order to protect against insider threats and maintain continuous regulatory compliance.

Organizations typically struggle with finding a central identity repository for non-employee Identities that may encompass contractors, contingent works, partners, or devices and services.
Anomalix offers a cloud-based Identity repository that is purpose-built to catalog and manage any Identity type. Flexible administration options allow for manual and automated data loads. Changes in Identity attributes and events are actionable to include notifications as well as automated access changes.

Access Governance is the process of monitoring and controlling who within your organization has access to what, when, and how. Access governance extends beyond merely managing access rights to defining security processes and policies that can impact an enterprise’s management of data assets. The monitoring of access includes not only access to business-critical applications but also hardware, infrastructure, and the network itself.

In addition to physical and virtual tokens, Anomalix offers intelligent risk-based authentication and access control solutions using supervised and unsupervised algorithms that determine when an additional form of authentication is required. On-premise and Cloud applications are protected by ensuring three key factors:
Quickly determine when to deny access based on anomalous activity derived from Identity, Device, and Behavior analytics that are evaluated by the software in real-time to enable only trusted access to organizational resources and data.


Role-Based Access Control (RBAC) allows users to access exactly what they need in order to do the activities defined by their role and eliminates the unnecessary security risks associated with giving a user more privilege than necessary.
RBAC is an identity management approach used to reduce manual access distribution across the enterprise and help to enforce the least privilege access required to perform job duties.
RBAC models leverage identity attributes to define role membership such as job function, locations, cost centers, etc., to mine and define roles. Automated access changes are initiated based on role membership changes. RBAC helps organizations to enable simplified access management, access certifications, and audit reporting across the enterprise.


Organizations are constantly looking for a way to enable central request, approval, and audit visibility for access to enterprise resources such as applications and data.
Anomalix helps organizations to establish a central request process that models the organizational business process for approvals and last-mile fulfillment.
Requests start with an intuitive end-user experience that guides them to physical or logical enterprise resources. Organizational and governance criteria drive access request approval workflows. After the necessary approvals take place, automated access provisioning to improve audit and security, as well as reduce the cost and error rates associated with manual access changes.

Now more than ever, organizations are charged with protecting sensitive and private information in many different ways; and demonstrating diligence in maintaining accurate inventories of personal data, where it resides, and how and where it is transmitted and handled.
Increasing advocacy and awareness has resulted in more pressure on organizations to provide customers with insight and the ability to request at any time how much of their personal data is being kept and how it is being used. As a result, regulators are also ramping up their scrutiny to ensure organizations can process information disclosure requests in a timely manner and honor customers’ “right to be forgotten.”

Automated User Provisioning is the underpinning for Identity Management solutions, as it enables automation of access changes and self-service capabilities. The notion of contextual access or Just-In-Time access is centered on Identity driven access changes.
Identity Registration
Provide automated onboarding for new users.
Delegated Administration
Enables administrators to assign Line-of-Business managers to make decisions about the level of access given to their direct report users, based on business logic and enabled through automated workflows.
Self-Service Identity Management
Allow end-users to manage their profile and credentials. Enable forgotten password resets without help-desk intervention.
Identity Lifecycle Management
Identity Lifecycle Management provides automated access changes when users move or transfer to different job responsibilities across that user’s different lifecycle states. Enable timely access revocation for planned or urgent terminations.